Divinum Fiat
Well-known member
Hi all,
For some unexplainable reason I got logged out of my forum and when I try logging back in I get the message "server error, please try again later."
The page is frozen at that error page and no matter what tabs I click, I can't move away from the error page.
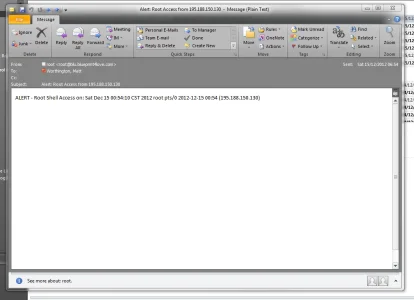
Does anyone have an idea of what this could be related to (my other domains, that share the same server, are up and running fine)?
For some unexplainable reason I got logged out of my forum and when I try logging back in I get the message "server error, please try again later."
The page is frozen at that error page and no matter what tabs I click, I can't move away from the error page.
Does anyone have an idea of what this could be related to (my other domains, that share the same server, are up and running fine)?