- Compatible XF 1.x versions
- 1.4
- 1.5
- License
- Commercial, Paid License
- Updates duration
- 6 months (renew for $8)
- Visible branding
- No
If you like this add-on, please >>rate it<<
Included in the [TAC] Total Anti-Spam Collection.
Description
Provides user-friendly automatic anti spam bot protection. Has no negative impact on users (compared to complicated or annoying types of CAPTCHA).
Currently Stops 100% of bots registering via the registration form. Bots will not be able to register via the registration form once installed.
It has multiple new methods for catching the new types of spam bots that started in 2017, which have successfully passed core honey pots.
Features
Stop bots from registering with elegant methods that do not bother humans (these mechanisms are described in more detail below):
Regardless of how good the built-in anti-bot mechanism of a particular forum software is, if it's too common then it becomes a target to break.
The customisation and variation provided by add-ons, such as this add-on, can help stop the vast majority of Forum Bots from registering.
How it works:
The Honey Pot Mechanism
This has not been used as a preventative mechanism for this plug-in, but for each bot that fails registration, this information is logged. Patterns of user_agent can give you more confidence that the bot detection is valid, but for a long time now, many bots fake the user_agent header to appear as if they are browsers.
Browser Plugin Detection
This has not been used as a preventative mechanism for this plug-in, but for each bot that fails registration, this information is logged. Users will usually have JavaScript enabled (bots will often not). By having JavaScript enabled, it is then possible to detect which plug-ins the browser supports.
Configure
Set options in the administration control panel: ACP -> Home -> Options -> FoolBotHoneyPot.
Feedback
There is a constant arms race between spam bots and anti-spam tools. It is therefore possible that a spam bot could evolve to defeat this add-on. If such a thing eventuates, please submit the logs and details of the false negative (the bot that got through), and the matter will be investigated.
Screenshots
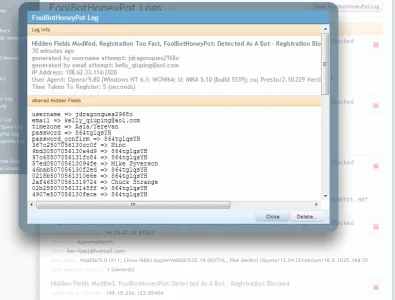
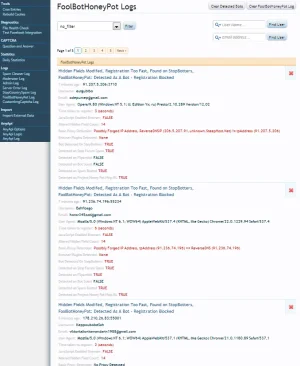
Included in the [TAC] Total Anti-Spam Collection.
Description
Provides user-friendly automatic anti spam bot protection. Has no negative impact on users (compared to complicated or annoying types of CAPTCHA).
Currently Stops 100% of bots registering via the registration form. Bots will not be able to register via the registration form once installed.
It has multiple new methods for catching the new types of spam bots that started in 2017, which have successfully passed core honey pots.
Features
Stop bots from registering with elegant methods that do not bother humans (these mechanisms are described in more detail below):
- Various types of hidden honey pot traps (and other types of honey pots that are not hidden fields).
- StopBotters API request to detect known Bots (optional and logged).
- JavaScript Detection (optional and logged).
- Dynamically ordered registration fields.
- Registration Field names which are different for every session.
- Basic Proxy Detection (logged).
- User Agent (logged).
- Browser Plugin Detection (logged).
- Detected as Non Browser Bot
- Detected as Browser Bot
- Detected as Semi Automation
- The methods for these will not be disclosed (to mitigate spammer research), they just simply detect the new types of bots.
- Works with the free add-on [TAC] Any Spam Api (designed for this add-on, but can be used as a stand alone), so any supplementary API you want can be added to prevent registration.
Note: even without AnyApi, this add-on currently blocks 100% of bots.
- Any Spam Api (Use any API you want, to prevent spam bots / spam humans from registering)
- Stop Human Spam (Stops humans creating links / sigs / banned content, it also checks for "sneaky broken links")
- Stop Country Spam (to reduce spam from particular countries; bot/human),
- Custom Image Captcha(as a second wave fallback mechanism),
- Recommended with this add-on, since Fool Bot Honey Pot will also unlock some of [TAC] Custom Image Captchas features.
- Bot Arrestor (to reduce the amount of resources spam bots use)
Regardless of how good the built-in anti-bot mechanism of a particular forum software is, if it's too common then it becomes a target to break.
The customisation and variation provided by add-ons, such as this add-on, can help stop the vast majority of Forum Bots from registering.
How it works:
The Honey Pot Mechanism
- XRumer and other bots will often try to register by sending a request directly to the registration form (carrying over the session cookie). In order to populate the form, the bots will use field names. Text is then injected into the field values containing that name (this process is written into a script / used by a standard script against XenForo registration). These field names will often be standard field names such as name = "name", name = email, name = password, etc.
- With the Honey Pot Mechanism, these fields still exist but are hidden (from humans). A bot will automatically fill these fields, but by doing so the bot has been fooled by the "honey pot" and is subsequently caught and prevented from registering.
- Additionally, XRumer bot users will sometimes write the script so that all form fields are populated, this will of course be caught by the standard honey pots. So there are multiple other supplementary hidden trick fields that will catch these bots, and these fields are named with UUIDs that are created on the fly for each session.
- As mentioned above, XRumer and many other bots will try to inject information into forms by using fields names that it knows (name=email, name=password).
- With the customisation mechanism, each of the valid field names (the fields that a user can see) are now uniquely named, and new names are created for each session.
- Since the bot will not know which fields names are which (for instance which is the email and which is the password_confirm) it makes it incredibly difficult for the bot to know how to populate the form correctly, once again preventing the bot from registering.
- For those bots that do not use fields names, but simply populate the form according to form index order, this is an additional mechanism to trip them up.
- By randomising the field order, it makes it incredibly hard to populate a form according to index number.
- The fields are randomised every time the registration page is loaded/refreshed.
- Although this is fairly rare, some bots that target forum software do not always post data where the form tells them to, but POST data to where they expect the core to be located. For instance, the core data will usually be posted to yoursite.com/register/register.
- By adding an URL param and value and only accepting the data posted to yoursite.com/register/register&xxx=yyy, we can stop these type of bot attempts (this acts like an extra hidden field).
- Both the Param and Values are UUIDs that change with every session attempt, making the URL effectively dynamic.
- Stops a high percentage of known bots using an API request.
- Known bots are detected via IP address / email address / username.
- The underlying StopBotters mechanism is confidential.
- This registration prevention method is optional (defined in the ACP).
- As you probably know, many bots are simply applications running scripts. They do not have their own JavaScript version, they simply fake what they can.
- This method detects the availability of JavaScript by sending an Ajax request at the time of registration.
- If no Ajax request is made, then the browser does not have JavaScript enabled (and has a high potential of being a bot).
- This information is logged for bots, but there is also the option (in the ACP) whether or not to allow users that do not have JavaScript Enabled to register.
- If a genuine user attempts to register without JavaScript enabled, they are presented with an error asking them to enable JavaScript.
- At the time of writing this, approximately 98% of users have JavaScript enabled by default (and it's even higher in certain countries).
- This has not been used as a preventative mechanism for this plug-in, but for each bot that fails registration, this information is logged. There are many ways of detecting proxies, but none of them are fool proof. One mechanism is to detect open ports (some times known as 'scanning back'). However, this is time consuming (can take between 1-3 seconds or longer for each port), since bots can use any port ranging from 0 to 65535, and will often use rare / non standard ports. Therefore, this type of detection has not been used.
- Instead the headers have been checked for known proxy variables (this catches mainly transparent proxies).
- Additionally, proxies are detected with a ReverseDNS Look up (catches some anon / high-anon proxies).
- Additionally, proxies are detected by comparing the ReverseDNS IP address to the hostname for that IP address (catches some anon / high-anon proxies).
- After testing this, approximately 70% of bots were found to be using proxies that were easy to detect using these proxy detection mechanisms (so this may be added as an optional preventative mechanism).
This has not been used as a preventative mechanism for this plug-in, but for each bot that fails registration, this information is logged. Patterns of user_agent can give you more confidence that the bot detection is valid, but for a long time now, many bots fake the user_agent header to appear as if they are browsers.
Browser Plugin Detection
This has not been used as a preventative mechanism for this plug-in, but for each bot that fails registration, this information is logged. Users will usually have JavaScript enabled (bots will often not). By having JavaScript enabled, it is then possible to detect which plug-ins the browser supports.
Configure
Set options in the administration control panel: ACP -> Home -> Options -> FoolBotHoneyPot.
Feedback
There is a constant arms race between spam bots and anti-spam tools. It is therefore possible that a spam bot could evolve to defeat this add-on. If such a thing eventuates, please submit the logs and details of the false negative (the bot that got through), and the matter will be investigated.
Screenshots


- Related resources