The options are there to turn off the logs / reduce the amount of logging information
By default, it doesn't log multiple attempts from the same IP address... otherwise you would be getting a lot more (but you can turn this on if you like)
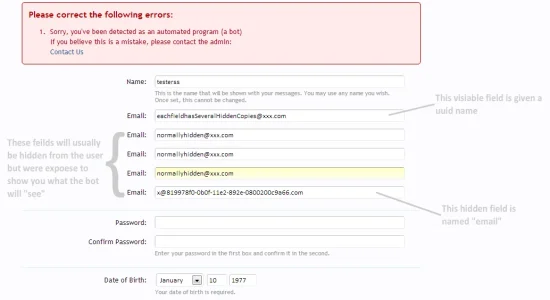
However, from the logs, if you click each entry, you can almost see straight away that they are bots, since they will often fill lots of hidden fields with random strings:
PHP:
a:14:{
s:8:"username";s:7:"jywcnhl"; // hidden honey pot
s:5:"email";s:27:"levijohnston917@yahoo.co.uk"; // hidden honey pot
s:8:"timezone"; s:11:"Asia/Almaty"; // hidden honey pot
s:8:"password";s:10:********"; // hidden honey pot
s:16:"password_confirm";s:10:"********"; // hidden honey pot
s:18:"367c2507056130cc0f";s:14:"Ramon Gonzales"; // hidden honey pot
s:18:"9bd30507056130a4d9";s:10:"Ajasonde12"; // hidden honey pot
s:18:"97c68507056131fc84";s:10:"Ajasonde12"; // hidden honey pot
s:18:"57ed050705613094fe";s:15:"Randall Nedescu"; // hidden honey pot
s:18:"46bab507056130f2ed";s:10:"Ajasonde12"; // hidden honey pot
s:18:"0218b5070561310e6e";s:10:"Ajasonde12"; // hidden honey pot
s:18:"2af465070561319724";s:12:"Im a Spammer"; //<< omg! this bot really put that
s:18:"02b2550705613148ff";s:10:"Ajasonde12"; // hidden honey pot
s:18:"4907e507056130fece";s:10:"Ajasonde12"; // hidden honey pot
}
Why would a human need to fill so many hidden fields with the text "Ajasonde12" ?
[PS I don't feel particularly bad about exposing bot passwords, even if they use this account on many fourms]
Note: they do not always fill out all the honey pots, sometimes they just target XF and fill out what they expect to see (they would then obviously also fail on a custom catpcha test, since this field would not be expected to be there). What they often do is fill out the cunning honey pots named "username/email/.. etc", they do not know that the real fields are named with uuids
You can also google the username / ip address and email address... and most of the time (but not always) these are old circulating bots picked up by stopforumspam etc...
The great thing is, this doesn't just catch bots that are already known (which will be
implemented in XF 1.2) but it catches bots that are not known yet, so this will continue to be useful for a while.
Code:
Registration Blocked: User blocked from registering
Today at 10:22 AM
generated by username attempt: jywcnhl
generated by email attempt: levijohnston917@yahoo.co.uk
IP Address: 91.236.74.197
I still highly recommend using this with the free resource CustomImgCaptcha, they work pretty well hand in hand. I've had bots that at least atempt the custom CAPTCHA, but none that pass them yet (I also havent had any humans that fail the CAPTCHA, apart from when clickfinity put no anwser for "spoon" ^^ <tuts>)
This works well on its own, but it's nice to see real stats for CATPCHA for human fails and what CAPTCHAs bots can pass, this makes it very easy to "prune" CAPTCHA images