Jonathan_Bathrough
Member
- Affected version
- 2.3.6
Hello,
template "register_form" contains:
template "login" contains:
Captcha is enabled:
Issue Description:
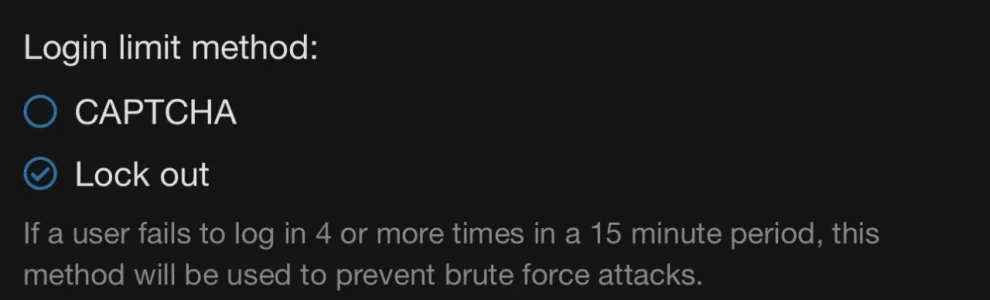
When "Enable CAPTCHA for guests" is set up CAPTCHA is displayed and validated correctly on the sign-up (registration) page. However, on the sign-in (login) page, no CAPTCHA is displayed.
If the conditional <xf:if is="$captcha"> is removed from the "login" template, the CAPTCHA widget becomes visible. However, the CAPTCHA response is not validated on form submission, allowing login to proceed without requiring a correct CAPTCHA solution.
Expected Behavior:
CAPTCHA should appear on the login form when enabled in options ("Enable CAPTCHA for guests"), and the CAPTCHA response should be validated properly to prevent login if the CAPTCHA is incorrect.
template "register_form" contains:
XML:
<xf:captcharow label="{{ phrase('verification') }}" hint="{{ phrase('required') }}" context="xf_register" />template "login" contains:
XML:
<xf:if is="$captcha">
<xf:captcharow label="{{ phrase('verification') }}" force="true" force-visible="true" context="xf_login" />
</xf:if>Captcha is enabled:
Code:
Setup -> Options -> User registration
"Enable CAPTCHA for guests" is set up to Use hCaptchaIssue Description:
When "Enable CAPTCHA for guests" is set up CAPTCHA is displayed and validated correctly on the sign-up (registration) page. However, on the sign-in (login) page, no CAPTCHA is displayed.
If the conditional <xf:if is="$captcha"> is removed from the "login" template, the CAPTCHA widget becomes visible. However, the CAPTCHA response is not validated on form submission, allowing login to proceed without requiring a correct CAPTCHA solution.
Expected Behavior:
CAPTCHA should appear on the login form when enabled in options ("Enable CAPTCHA for guests"), and the CAPTCHA response should be validated properly to prevent login if the CAPTCHA is incorrect.