ActorMike
Well-known member
- Affected version
- 2.x
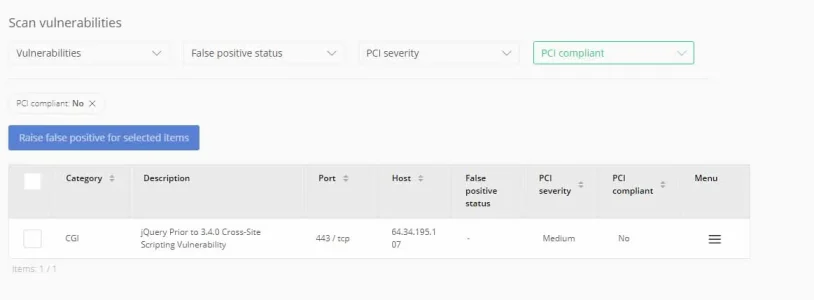
I did my PCI compliance scan today and it failed because we are using a version of JQuery prior to 3.4.0
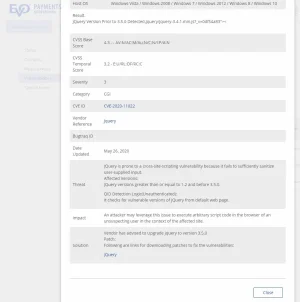
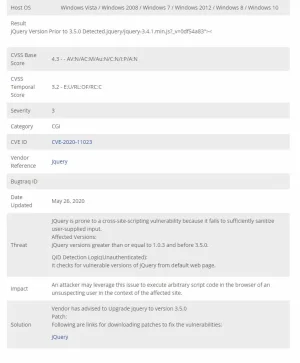
jQuery Prior to 3.4.0 Cross-Site Scripting Vulnerability- http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358
Is it okay to manually update it, or will it crash the forum?
Mike

jQuery Prior to 3.4.0 Cross-Site Scripting Vulnerability- http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11358
Is it okay to manually update it, or will it crash the forum?
Mike

Web Design Knoxville | Website World Web Design Knoxville
Building better Knoxville TN websites since 1998! Best freelance website designers and web design agencies.
websiteworld.com
Last edited: