PumpinIron
Well-known member
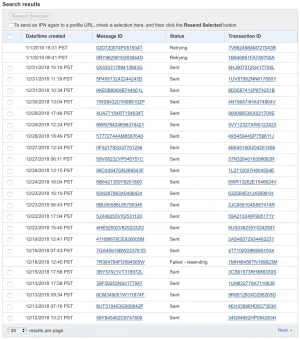
I’m running the latest stable version of XenForo, but as of today I just received the following email from PayPal:
Please check your server that handles PayPal Instant Payment Notifications (IPN). IPNs sent to the following URL(s) are failing:
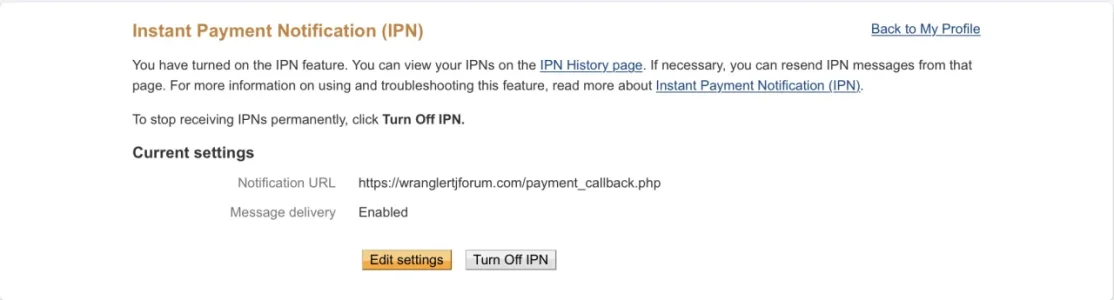
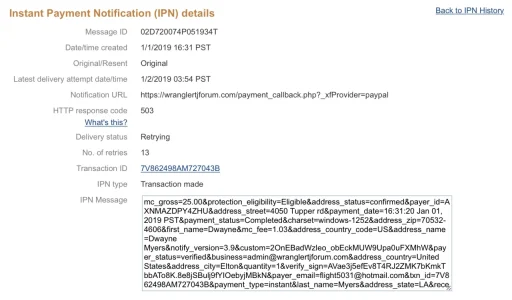
https://wranglertjforum.com/payment_callback.php?_xfProvider=paypal
If you do not recognize this URL, you may be using a service provider that is using IPN on your behalf. Please contact your service provider with the above information. If this problem continues, IPNs may be disabled for your account.
Thank you for your prompt attention to this issue.
Thanks,
PayPal
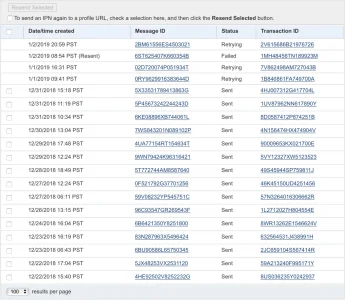
I checked the address and this isn’t a phishing scam, it’s a legit email from PayPal. What I can’t figure out is why I am getting this email. I have used upgraded enabled and the @AddonFlare “Paid Registrations” add-on which uses PayPal as well.
I’ve never once had an issue with a payment going through though, and I don’t see anything in the logs about it, so I’m really confused as to what’s going on.
Please check your server that handles PayPal Instant Payment Notifications (IPN). IPNs sent to the following URL(s) are failing:
https://wranglertjforum.com/payment_callback.php?_xfProvider=paypal
If you do not recognize this URL, you may be using a service provider that is using IPN on your behalf. Please contact your service provider with the above information. If this problem continues, IPNs may be disabled for your account.
Thank you for your prompt attention to this issue.
Thanks,
PayPal
I checked the address and this isn’t a phishing scam, it’s a legit email from PayPal. What I can’t figure out is why I am getting this email. I have used upgraded enabled and the @AddonFlare “Paid Registrations” add-on which uses PayPal as well.
I’ve never once had an issue with a payment going through though, and I don’t see anything in the logs about it, so I’m really confused as to what’s going on.