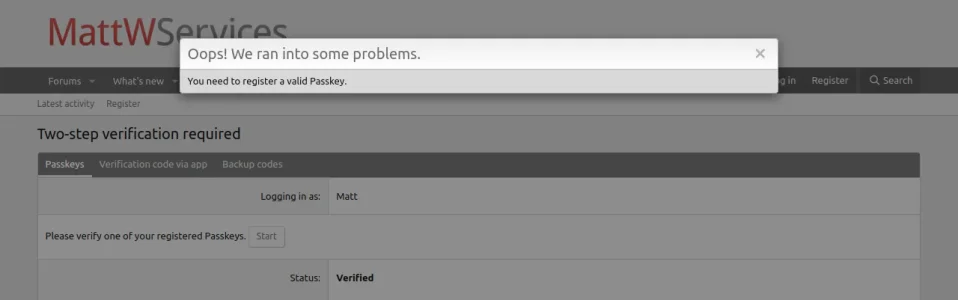
1. There is nothing that will link your physical phone. You also wouldn't want to, because you would be locked out of your accounts if it broke, got upgraded to a new phone, dropped in a river, etc. You
can use your phone as a security key (also known as a Passkey), but it's not bound to your physical phone, in that case it's linked to your Apple ID (any device that you are logged into your Apple ID would work, not just the one device you set it up with originally). If you aren't seeing anything for Passkeys, are you maybe using an older version of iOS (it was a fairly recent addition in iOS 16.x)?
2. Right... like you said, you answered your own question. It wouldn't make sense to go out of your way to remove the ability for users to secure their account if they so choose. They don't have to do it, but why go out of your way to remove the option for them? Wouldn't make much sense.