Siropu
Well-known member
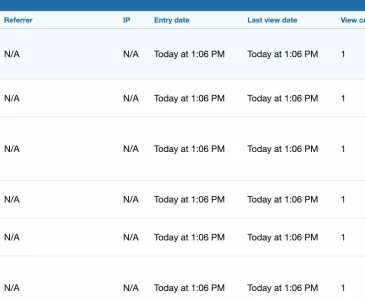
Add-on logs all 404 when they occur so that's strange.I have an issue with it showing me TAGS in the logs (thousands of them), and when I click on them, it takes me to the TAG page and not a 404.
There is an admin option for regex redirects.is there a way to set up the 404 redirects's using a wildcard url to capture all possible combo's