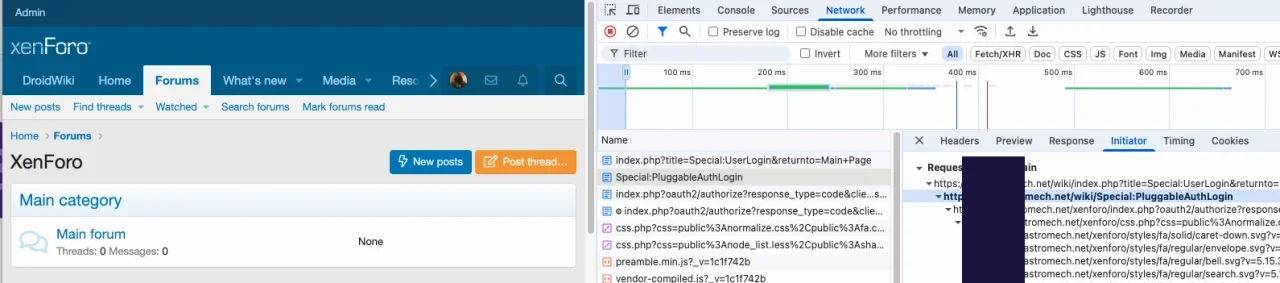
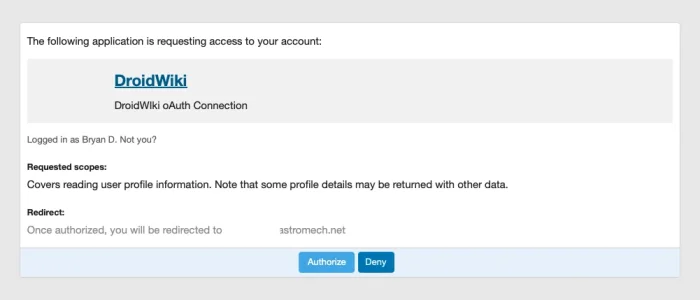
I'm new to XenForo; our whole forum is moving to XenForo from vBulletin in the next few weeks. We have run into a problem with OAuth talking to MediaWiki. So, after a lot of debugging and troubleshooting, I tried a different solution, using WordPress as an OAuth client and XenForo as the OAuth provider. I end up with the same problem. Data is not being sent back to MediaWiki or WordPress. I also tested via curl and Postman; all results were the same.
I'm trying to find a few things.
1) Any logs related to OAuth on XenForo
2) Is there a further configuration outside of the OAuth that I need to enable on the XenForo side?
3) Is there a better way to troubleshoot XenForo Oauth as a provider?
Error message example
Invalid response received from Auth Provider. Contact your administrator for more details.
Response :
{ "message": "Sorry, we're currently unavailable. Please check back later." }
WordPress:
Error
Token Response Received = {
MediaWiki
For MediaWiki I am using the Extensions PluggableAuth and WSOAuth. For WSOAuth I had to build a custom XenForo provider. If I can get this all working, I hope to share it with the world.
Error
The username provided by the OAuth provider is not valid.
Further logging resulting in this
*Token URI during construction: NULL
*Failed to decode token response: Syntax error
*Raw Token Response: false
Thanks in advance for any help or ideas you can share.
I'm trying to find a few things.
1) Any logs related to OAuth on XenForo
2) Is there a further configuration outside of the OAuth that I need to enable on the XenForo side?
3) Is there a better way to troubleshoot XenForo Oauth as a provider?
Error message example
Invalid response received from Auth Provider. Contact your administrator for more details.
Response :
{ "message": "Sorry, we're currently unavailable. Please check back later." }
WordPress:
Error
Token Response Received = {
MediaWiki
For MediaWiki I am using the Extensions PluggableAuth and WSOAuth. For WSOAuth I had to build a custom XenForo provider. If I can get this all working, I hope to share it with the world.
Error
The username provided by the OAuth provider is not valid.
Further logging resulting in this
*Token URI during construction: NULL
*Failed to decode token response: Syntax error
*Raw Token Response: false
Thanks in advance for any help or ideas you can share.