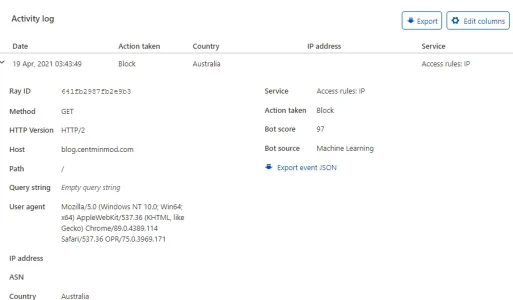
./cf-analytics-graphql.sh rayid-hrs 1 641fb2987fb2e9b3
------------------------------------------------------------------
Cloudflare Firewall
------------------------------------------------------------------
since: 2021-04-18T17:03:24Z
until: 2021-04-18T18:03:24Z
------------------------------------------------------------------
1 Firewall Events for CF RayID: 641fb2987fb2e9b3
------------------------------------------------------------------
1 xxx.xxx.xxx.xxx 403 97xMachine Learning block ASN# ISP-NAME ISP AU BNE GET HTTP/2 ip
------------------------------------------------------------------
1 xxx.xxx.xxx.xxx 403 97xMachine Learning block ASN# ISP-NAME ISP AU BNE GET HTTP/2
------------------------------------------------------------------
1 xxx.xxx.xxx.xxx 403 97xMachine Learning block ASN# ISP-NAME ISP AU BNE blog.centminmod.com GET HTTP/2
------------------------------------------------------------------
1 xxx.xxx.xxx.xxx 403 97xMachine Learning block ASN# ISP-NAME ISP AU BNE blog.centminmod.com GET HTTP/2 /
------------------------------------------------------------------
xxx.xxx.xxx.xxx 641fb2987fb2e9b3 403 97xMachine Learning block ASN# ISP-NAME ISP AU BNE 2021-04-18T17:43:49Z blog.centminmod.com GET HTTP/2 /
------------------------------------------------------------------
{
"results": [
{
"action": "block",
"botScore": 97,
"botScoreSrcName": "Machine Learning",
"clientASNDescription": "ISP-NAME ISP",
"clientAsn": "ASN#",
"clientCountryName": "AU",
"clientIP": "xxx.xxx.xxx.xxx",
"clientRefererHost": "blog.centminmod.com",
"clientRefererPath": "/2020/09/06/203/wordpress-cache-enabler-advanced-full-page-caching-guide/",
"clientRefererQuery": "",
"clientRefererScheme": "https",
"clientRequestHTTPHost": "blog.centminmod.com",
"clientRequestHTTPMethodName": "GET",
"clientRequestHTTPProtocol": "HTTP/2",
"clientRequestPath": "/",
"clientRequestQuery": "",
"clientRequestScheme": "https",
"datetime": "2021-04-18T17:43:49Z",
"edgeColoName": "BNE",
"edgeResponseStatus": 403,
"kind": "firewall",
"originResponseStatus": 0,
"rayName": "641fb2987fb2e9b3",
"ruleId": "ip",
"source": "ip",
"userAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36 OPR/75.0.3969.171"
}
]
}