Alright, no worries, take your time. I didn't want to bother doing the edits myself as I can see this addon is updated often. I will probably buy this soon.I'll take a look, but it might not be a simple as just turning it off for registration, I don't want to add bugs where they dont need to exist, but if I can do this without complications, I'll add your suggestion as an ACP option
I'll add it to the "to-do list" and will take a look when I get a chance
I have a couple more things that I want to add to this 1st (which might take a few days)
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
[TAC] Fool Bot Honey Pot [Paid] 3.0.32
No permission to buy ($29.00)
- Thread starter tenants
- Start date
CTXMedia
Well-known member
Suggestion: Reconfigure the .zip install files to be compatible with Chris Deeming's Add-On Installer/Upgrader. With the frequency of updates, it will make upgrading a lot easier
TBH that's not a bad suggestion - I noticed the files were packaged differently with this add-on, but because I knew where they should all go I didn't really bother mentioning it - but if more people are going to be using it, it would be good to organised the package the same way as others.
Can you please add the following Xenforo bugfix into your next release? It will save me a file edit after each upload and also help other people with that XenForo bug. 
http://xenforo.com/community/threads/required-custom-fields-can-be-skipped-on-registration.41413/
You need to modify FoolBotHoneyPot_ControllerPublic_Register.
THANK YOU!
http://xenforo.com/community/threads/required-custom-fields-can-be-skipped-on-registration.41413/
You need to modify FoolBotHoneyPot_ControllerPublic_Register.
THANK YOU!
fixing core issues in plugins
Okay, will do
I know it is strange, but given the current situation at XF....
See it as a service to your customers.
tenants
Well-known member
tenants updated FoolBotHoneyPot Bot Killer: Spam Combat with a new update entry:
FoolBotHoneyPot - v2.0.09 - Required custom fields are now always validated serverside
Read the rest of this update entry...
FoolBotHoneyPot - v2.0.09 - Required custom fields are now always validated serverside
- Fixed the core issue related to custom fields not actually being required (for bots)
- Rearranged zip to work with Chris Deeming's plugin uploader
Read the rest of this update entry...
A few things that bothered me:
The phrase that says you were detected as a bot and offers a link to the contact page is a hard coded link, so even with friendly URLs on you'll see the index.php in the URL. Maybe generate the link and pass the param to the phrase? I would assume most people wouldn't care about this, so it's up to you if you want to fix it or not.
Another thing I noticed is that in firefox I'm seeing 2 fieldset borders (thin blue lines) after the username and password. I imagine this has to do with hidden fields. This doesn't happen in Chrome though. More annoyingly, due to these hidden fields I'm not able to properly tab to the next fields. I'm not sure about most people, but when I'm filling in forms I tend to fill in the field, tab to the next, fill in, tab, and repeat until completed. It can be a hassle when you need to press tab 3 times to get to the next field.
After realising that tabbing appears to be hitting the hidden fields I decided to try randomly typing something while tabbing into them and was detected as a bot with altering hidden fields. So if a user is typing in his fields relatively quickly and doesn't pay attention to the fact that he didn't actually tab to the next field correctly and starts typing, they'll end up being detected as a bot. :S Anyone else able to reproduce this?
The phrase that says you were detected as a bot and offers a link to the contact page is a hard coded link, so even with friendly URLs on you'll see the index.php in the URL. Maybe generate the link and pass the param to the phrase? I would assume most people wouldn't care about this, so it's up to you if you want to fix it or not.
Another thing I noticed is that in firefox I'm seeing 2 fieldset borders (thin blue lines) after the username and password. I imagine this has to do with hidden fields. This doesn't happen in Chrome though. More annoyingly, due to these hidden fields I'm not able to properly tab to the next fields. I'm not sure about most people, but when I'm filling in forms I tend to fill in the field, tab to the next, fill in, tab, and repeat until completed. It can be a hassle when you need to press tab 3 times to get to the next field.
After realising that tabbing appears to be hitting the hidden fields I decided to try randomly typing something while tabbing into them and was detected as a bot with altering hidden fields. So if a user is typing in his fields relatively quickly and doesn't pay attention to the fact that he didn't actually tab to the next field correctly and starts typing, they'll end up being detected as a bot. :S Anyone else able to reproduce this?
tenants
Well-known member
hmmm...
The phrase isnt hard coded, it can be found in your phrases as: foolbothoneypot_sorry_youve_been_detected_as_an_automated_program
However, I can pass in the url link to the phrase, so it uses the correct contact url (with/without the index.php)
Tabing is a bit unavoidable
But, if they do tab and access hidden fields and if they then fill in those hidden fields they aren't blocked permantantly,
they're told they've been detected and redirect to the registration page to re-attempt the form (and the hidden fields are reset)... I can't prevent tabbing ( I can't really set a tabbing order, since this could then be used by bots)
I've found that there are only 3 fields that are accessed by tabs (out of 24 hidden fields) and that's because they are not diplsay:none, but hidden/shrunk. For those 3 fields, I can set them so they can't be selected (so can't be changed by humans). That should prevent humans changing the values of these particular hidden fields and ever seeing the message for bots.
Having various different methods of hidding fields is part of how the honey pot works (So I don't want to hide all of these fields with the same method)
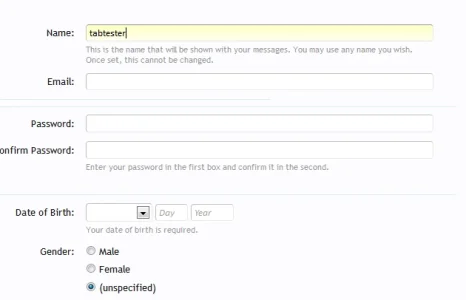
I'll look into the cosmetic blue lines in FireFox... (do you have a screen cap, I can't see them in FireFox myself)
The phrase isnt hard coded, it can be found in your phrases as: foolbothoneypot_sorry_youve_been_detected_as_an_automated_program
However, I can pass in the url link to the phrase, so it uses the correct contact url (with/without the index.php)
Tabing is a bit unavoidable
But, if they do tab and access hidden fields and if they then fill in those hidden fields they aren't blocked permantantly,
they're told they've been detected and redirect to the registration page to re-attempt the form (and the hidden fields are reset)... I can't prevent tabbing ( I can't really set a tabbing order, since this could then be used by bots)
I've found that there are only 3 fields that are accessed by tabs (out of 24 hidden fields) and that's because they are not diplsay:none, but hidden/shrunk. For those 3 fields, I can set them so they can't be selected (so can't be changed by humans). That should prevent humans changing the values of these particular hidden fields and ever seeing the message for bots.
Having various different methods of hidding fields is part of how the honey pot works (So I don't want to hide all of these fields with the same method)
I'll look into the cosmetic blue lines in FireFox... (do you have a screen cap, I can't see them in FireFox myself)

tenants
Well-known member
oh wait.. looking at the above screen cap again, I do see them, the 2 faint lines after the email field? (there should only be one)
... okay, I've fixed the url issue for the contact link (for the bots warning message)
... I've made it so that the tabbed fields can't be altered (but you may sometimes have to tab a couple of times to get to the next field, this can't be avoided)
... I'll look at those blue lines now
... okay, I've fixed the url issue for the contact link (for the bots warning message)
... I've made it so that the tabbed fields can't be altered (but you may sometimes have to tab a couple of times to get to the next field, this can't be avoided)
... I'll look at those blue lines now
tenants
Well-known member
tenants updated FoolBotHoneyPot Bot Killer: Spam Combat with a new update entry:
FoolBotHoneyPot v2.0.10 - Minor Fixes: FF Cosmetic, Tabbing and Contact URL
Read the rest of this update entry...
FoolBotHoneyPot v2.0.10 - Minor Fixes: FF Cosmetic, Tabbing and Contact URL
- Fields that can be tabbed into can no longer have their value changed
- The error message seen by bots now has the link passed into the phrase (avoids index.php when applicable)
- FireFox cosmetic issue (thin blue line under the email field on registration form) has been fixed
Read the rest of this update entry...
Thanks for fixing those issues so quickly. 
About the hidden fields that can be tabbed, since you mentioned there is only 3 of them, how about an option for setting these 3 on and off? Maybe it's just me, but I find this to be quite a big usability issue. The reason I like this is addon is right in the description, "Stop bots from registering with elegant methods that do not bother humans" but this tabbing issue can bother some humans. You could set an option to display these 3 fields with it defaulting to on and most forums would have maximum protection, but for the really picky they might choose to turn off these 3 fields even if it may result in a few bots that slip through. Since most bots seem to be altering at least 14 of the fields I'm willing to sacrifice a bit if it can resolve this tabbing issue. Considering that I also have to use captcha right now, I would hope the captcha would catch any remaining ones that do pass the FBHP.
You could set an option to display these 3 fields with it defaulting to on and most forums would have maximum protection, but for the really picky they might choose to turn off these 3 fields even if it may result in a few bots that slip through. Since most bots seem to be altering at least 14 of the fields I'm willing to sacrifice a bit if it can resolve this tabbing issue. Considering that I also have to use captcha right now, I would hope the captcha would catch any remaining ones that do pass the FBHP.
Edit:
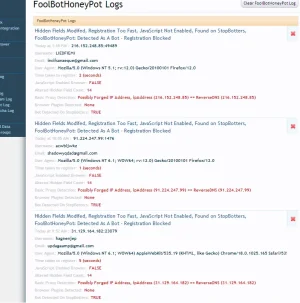
In a separate issue, I noticed in one of the logs:
Basic Proxy Detection: Proxy Headers Found: $_SERVER[HTTP_PROXY_CONNECTION]: Keep-Alive
Is that server variable not being parsed, or is that correct?
About the hidden fields that can be tabbed, since you mentioned there is only 3 of them, how about an option for setting these 3 on and off? Maybe it's just me, but I find this to be quite a big usability issue. The reason I like this is addon is right in the description, "Stop bots from registering with elegant methods that do not bother humans" but this tabbing issue can bother some humans.
Edit:
In a separate issue, I noticed in one of the logs:
Basic Proxy Detection: Proxy Headers Found: $_SERVER[HTTP_PROXY_CONNECTION]: Keep-Alive
Is that server variable not being parsed, or is that correct?
tenants
Well-known member
That is correct, that is the proxy header that was detect. The bot is using a proxy, and it's a traparent proxy...Edit:
In a separate issue, I noticed in one of the logs:
Basic Proxy Detection: Proxy Headers Found: $_SERVER[HTTP_PROXY_CONNECTION]: Keep-Alive
Is that server variable not being parsed, or is that correct?
Most bot proxys will be detected as:
OrPossibly Forged IP Address, ReverseDNSIP (somehostname) != ipAddress (xxx.xxx.xxx.xxx)
These 2 methods seem to pick up about 70% of the bot proxies.... and these are often Anonym / High Anonym (not transparent)Possibly Forged IP Address, ipAddress (xxx.xxx.xxx.xxx) == ReverseDNS (xxx.xxx.xxx.xxx)
For the transparent proxies, I check the header for the following:
'HTTP_VIA', 'HTTP_X_FORWARDED_FOR', 'HTTP_FORWARDED_FOR', 'HTTP_X_FORWARDED',
'HTTP_FORWARDED', 'HTTP_CLIENT_IP', 'HTTP_FORWARDED_FOR_IP', 'VIA',
'X_FORWARDED_FOR', 'FORWARDED_FOR', 'X_FORWARDED', 'FORWARDED',
'CLIENT_IP', 'FORWARDED_FOR_IP', 'HTTP_PROXY_CONNECTION'
If any of the transparents are found, I list them and let you know with the following string:
Proxy Headers Found: $_SERVER['header_index_name']: header value
In your case
Basic Proxy Detection: Proxy Headers Found: $_SERVER[HTTP_PROXY_CONNECTION]: Keep-Alive
The transparent proxies are fairly rare (they kind of defeat the object of using a proxy, since they are easy to detect), but every now and then one pops up. They're almost always free and available, so if a bot user wants to cut corners and not spend any more money / uses a bad list of proxies then sometimes they use transparent proxies (often without realising)
The $_SERVER is not a variable, that's here on purpose, since "HTTP_PROXY_CONNECTION" is a $_SERVER index, and "Keep-Alive" is its value
About the hidden fields that can be tabbed, since you mentioned there is only 3 of them, how about an option for setting these 3 on and off?
That's a fair point, I could add this as an option.. I'll look at doing this next (within the next 5 days)
I see, thanks for clearing that up.The $_SERVER is not a variable, that's here on purpose, since "HTTP_PROXY_CONNECTION" is a $_SERVER index, and "Keep-Alive" is its value
Great, many thanks, I'll look forward to it.That's a fair point, I could add this as an option.. I'll look at doing this next (within the next 5 days)
tenants
Well-known member
tenants updated FoolBotHoneyPot Bot Killer: Spam Combat with a new update entry:
FoolBotHoneyPot v2.1.02 - StopBotters API
Read the rest of this update entry...
FoolBotHoneyPot v2.1.02 - StopBotters API
- Now makes use of StopBotters, this API will become increasing efficient at stopping bots with the more forums that use it.
Read the rest of this update entry...
Mouth
Well-known member
tenants updated FoolBotHoneyPot Bot Killer: Spam Combat with a new update entry:
- Now makes use of StopBotters, this API will become increasing efficient at stopping bots with the more forums that use it.
Is StopBotters yours?
Can I control the usage of it entirely, or individual checking of ip / email / username?
Why is stopbotters better than other spam/bot registration API's?
tenants
Well-known member
It might not be at first (but I've seen some promising results with a handful of forums)Why is stopbotters better than other spam/bot registration API's?
1) For one, it's not public... the data can't be used by people using bots. XRumer users are making use of the public data available (they switch parameters by doing a simple look up). With StopBotters they can not get to the StopBotters data.
2) You don't have to wait for the data to be manually reported. If bots are targeting XenForo, then all the bots that are targeting XenForo are targeted by this mechanism
3) One of the things I've noticed with XRumer is that some botters have started to avoid sites that are known for reporting to things like the StopForumSpam database (Xblack.txt)
If StopBotters was rolled out to many XenForo sites, each of the forums would be an automatic reporting site, so I could see a similar thing happening with all sites that use StopBotters
I can't really say much more about it right now.
You can just turn it off (there is a check box in the ACP)Can I control the usage of it entirely, or individual checking of ip / email / username?
In theory, the usage can be controlled, but in practice not this versions - I'll add a small update so:
1) You can check for IP Addresses or not (and the age at which this data is no longer relevant)
2) You can check for Email Addresses or not (I don't see why you would ever want to do this)
3) You can check for Usernames or not (I can see that this would be an option that some might want to use)