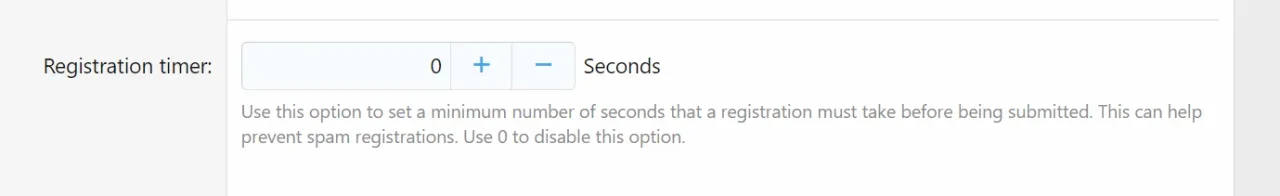
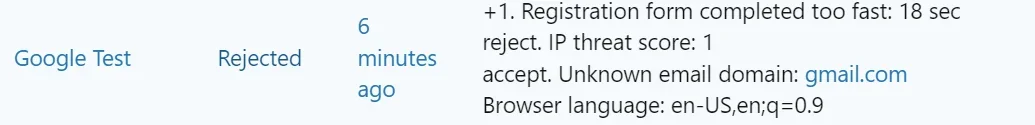
XF\Db\DuplicateKeyException: MySQL query error [1062]: Duplicate entry 'multiple_account-525343' for key 'content_type_content_id' src/XF/Db/AbstractStatement.php:230
Stack trace
INSERT INTO `xf_report` (`content_type`, `content_id`, `content_user_id`, `content_info`, `first_report_date`, `last_modified_date`, `last_modified_user_id`, `last_modified_username`, `report_id`, `report_state`, `assigned_user_id`, `comment_count`, `report_count`, `last_modified_id`) VALUES (?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?)
------------
#0 src/XF/Db/Mysqli/Statement.php(198): XF\Db\AbstractStatement->getException('MySQL query err...', 1062, '23000')
#1 src/XF/Db/Mysqli/Statement.php(79): XF\Db\Mysqli\Statement->getException('MySQL query err...', 1062, '23000')
#2 src/XF/Db/AbstractAdapter.php(96): XF\Db\Mysqli\Statement->execute()
#3 src/XF/Db/AbstractAdapter.php(220): XF\Db\AbstractAdapter->query('INSERT INTO `x...', Array)
#4 src/XF/Mvc/Entity/Entity.php(1514): XF\Db\AbstractAdapter->insert('xf_report', Array, false)
#5 src/XF/Mvc/Entity/Entity.php(1246): XF\Mvc\Entity\Entity->_saveToSource()
#6 src/XF/Service/Report/Creator.php(201): XF\Mvc\Entity\Entity->save(true, false)
#7 src/addons/SV/ReportImprovements/XF/Service/Report/CreatorPatch.php(58): XF\Service\Report\Creator->_save()
#8 src/XF/Service/ValidateAndSavableTrait.php(42): SV\ReportImprovements\XF\Service\Report\CreatorPatch->_save()
#9 src/addons/SV/SignupAbuseBlocking/Repository/MultipleAccount.php(352): XF\Service\Report\Creator->save()
#10 src/addons/SV/SignupAbuseBlocking/Repository/MultipleAccount.php(312): SV\SignupAbuseBlocking\Repository\MultipleAccount->reportCreator(Object(SV\SignupAbuseBlocking\Entity\LogEvent))
#11 src/addons/SV/SignupAbuseBlocking/Repository/MultipleAccount.php(239): SV\SignupAbuseBlocking\Repository\MultipleAccount->createNewReportEntries(Object(SV\SignupAbuseBlocking\Entity\LogEvent))
#12 src/addons/SV/SignupAbuseBlocking/Repository/MultipleAccount.php(63): SV\SignupAbuseBlocking\Repository\MultipleAccount->processMultipleAccountDetectionInternal(Object(SV\ElasticSearchEssentials\XF\Entity\User), Array, 'login')
#13 src/XF.php(618): SV\SignupAbuseBlocking\Repository\MultipleAccount->SV\SignupAbuseBlocking\Repository\{closure}()
#14 src/addons/SV/SignupAbuseBlocking/Repository/MultipleAccount.php(64): XF::asVisitor(Object(SV\ElasticSearchEssentials\XF\Entity\User), Object(Closure))
#15 src/addons/SV/SignupAbuseBlocking/XF/ControllerPlugin/Login.php(101): SV\SignupAbuseBlocking\Repository\MultipleAccount->processMultipleAccountDetection(Object(SV\ElasticSearchEssentials\XF\Entity\User), Array, 'login')
#16 src/XF/Pub/Controller/Login.php(115): SV\SignupAbuseBlocking\XF\ControllerPlugin\Login->completeLogin(Object(SV\ElasticSearchEssentials\XF\Entity\User), true)
#17 src/XF/Mvc/Dispatcher.php(352): XF\Pub\Controller\Login->actionLogin(Object(XF\Mvc\ParameterBag))
#18 src/XF/Mvc/Dispatcher.php(259): XF\Mvc\Dispatcher->dispatchClass('XF:Login', 'Login', Object(XF\Mvc\RouteMatch), Object(SV\SignupAbuseBlocking\XF\Pub\Controller\Login), NULL)
#19 src/XF/Mvc/Dispatcher.php(115): XF\Mvc\Dispatcher->dispatchFromMatch(Object(XF\Mvc\RouteMatch), Object(SV\SignupAbuseBlocking\XF\Pub\Controller\Login), NULL)
#20 src/XF/Mvc/Dispatcher.php(57): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch))
#21 src/XF/App.php(2351): XF\Mvc\Dispatcher->run()
#22 src/XF.php(517): XF\App->run()
#23 index.php(20): XF::runApp('XF\\Pub\\App')
#24 {main}