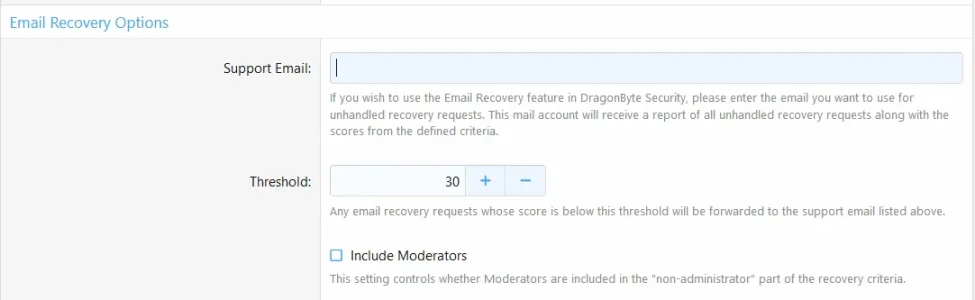
XF\Db\InvalidQueryException: Batch install error: xf_user_tfa_trusted: MySQL statement prepare error [1101]: BLOB, TEXT, GEOMETRY or JSON column 'dbtech_security_user_agent' can't have a default value src/XF/Db/AbstractStatement.php:217
Generated by: Nirjonmela Sep 19, 2019 at 9:36 PM
Stack trace
ALTER TABLE `xf_user_tfa_trusted`
CHANGE COLUMN `user_agent` `dbtech_security_user_agent` BLOB DEFAULT ''
------------
#0 src/XF/Db/Mysqli/Statement.php(196): XF\Db\AbstractStatement->getException('MySQL statement...', 1101, '42000')
#1 src/XF/Db/Mysqli/Statement.php(39): XF\Db\Mysqli\Statement->getException('MySQL statement...', 1101, '42000')
#2 src/XF/Db/Mysqli/Statement.php(54): XF\Db\Mysqli\Statement->prepare()
#3 src/XF/Db/AbstractAdapter.php(94): XF\Db\Mysqli\Statement->execute()
#4 src/XF/Db/Schema/AbstractDdl.php(151): XF\Db\AbstractAdapter->query('ALTER TABLE `xf...')
#5 src/XF/Db/SchemaManager.php(149): XF\Db\Schema\AbstractDdl->apply()
#6 src/addons/DBTech/Security/Setup.php(992): XF\Db\SchemaManager->alterTable('xf_user_tfa_tru...', Object(Closure))
#7 src/XF/AddOn/StepRunnerUpgradeTrait.php(122): DBTech\Security\Setup->upgrade904030051Step1(Array)
#8 src/XF/AddOn/StepRunnerUpgradeTrait.php(71): DBTech\Security\Setup->upgradeStepRunner(904030051, 1, Array, NULL)
#9 src/XF/Job/AddOnInstallBatch.php(297): DBTech\Security\Setup->upgrade(Array)
#10 src/XF/Job/AddOnInstallBatch.php(90): XF\Job\AddOnInstallBatch->stepAction(Object(XF\Timer))
#11 src/XF/Job/Manager.php(253): XF\Job\AddOnInstallBatch->run(G)
#12 src/XF/Job/Manager.php(195): XF\Job\Manager->runJobInternal(Array, G)
#13 src/XF/Job/Manager.php(111): XF\Job\Manager->runJobEntry(Array, G)
#14 src/XF/Admin/Controller/Tools.php(120): XF\Job\Manager->runByIds(Array, 8)
#15 src/XF/Mvc/Dispatcher.php(321): XF\Admin\Controller\Tools->actionRunJob(Object(XF\Mvc\ParameterBag))
#16 src/XF/Mvc/Dispatcher.php(244): XF\Mvc\Dispatcher->dispatchClass('XF:Tools', 'RunJob', Object(XF\Mvc\RouteMatch), Object(NF\Discord\XF\Admin\Controller\Tools), NULL)
#17 src/XF/Mvc/Dispatcher.php(100): XF\Mvc\Dispatcher->dispatchFromMatch(Object(XF\Mvc\RouteMatch), Object(NF\Discord\XF\Admin\Controller\Tools), NULL)
#18 src/XF/Mvc/Dispatcher.php(50): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch))
#19 src/XF/App.php(2178): XF\Mvc\Dispatcher->run()
#20 src/XF.php(390): XF\App->run()
#21 admin.php(13): XF::runApp('XF\\Admin\\App')
#22 {main}
Request state
array(4) {
["url"] => string(24) "/admin.php?tools/run-job"
["referrer"] => string(46) "https://nirjonmela.com/admin.php?tools/run-job"
["_GET"] => array(1) {
["tools/run-job"] => string(0) ""
}
["_POST"] => array(3) {
["_xfRedirect"] => string(81) "/admin.php?add-ons/install-from-archive-complete&batch_id=1"
["_xfToken"] => string(8) "********"
["only_ids"] => string(5) "95650"
}
}