Hi all, happy 2025!
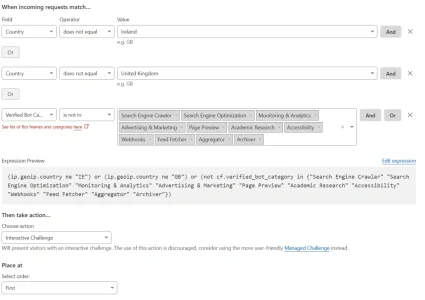
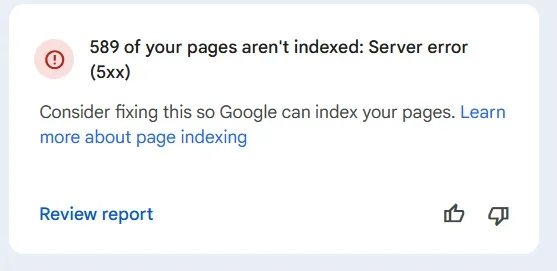
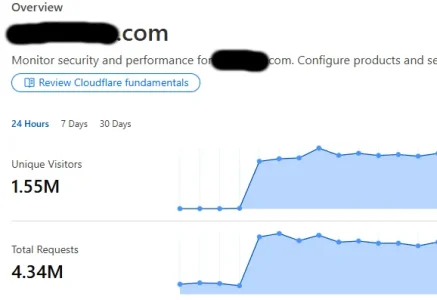
Our forum is small and never has over 20 registered users logged in, but recently it's been getting stuck due to 3000+ "Guests"/unregistered visitors arriving at the same time, which eventually triggers this error:
 i just really want the forum to be stable again.
i just really want the forum to be stable again.
I've set the forum not to display to unregistered users, but that makes no difference
I've checked access logs - user agents and IP addresses are not showing any obvious (to me anyway) culprits whose IP I could block
I've looked up the database error and found various obscure suggestions but i hope there may be a better way to sort this out than fiddling with the database?
Any suggestions would be very much appreciates, thanks in advance
Our forum is small and never has over 20 registered users logged in, but recently it's been getting stuck due to 3000+ "Guests"/unregistered visitors arriving at the same time, which eventually triggers this error:
- MySQL query error [1114]: The table 'xf_session_activity' is full
I've set the forum not to display to unregistered users, but that makes no difference
I've checked access logs - user agents and IP addresses are not showing any obvious (to me anyway) culprits whose IP I could block
I've looked up the database error and found various obscure suggestions but i hope there may be a better way to sort this out than fiddling with the database?
Any suggestions would be very much appreciates, thanks in advance