For anti-spam reasons, I want to know more about these js bots (which I believe to be mostly the latest xrummer), so next version I'll be adding debugging info so that I can't tell more about them
(you'll see a finger print option in the logs when you click a log entry if js is enabled for that bot/user)
At the moment we should wipe out both browser based bots and non browser based bots
(thats 100% of bots again)
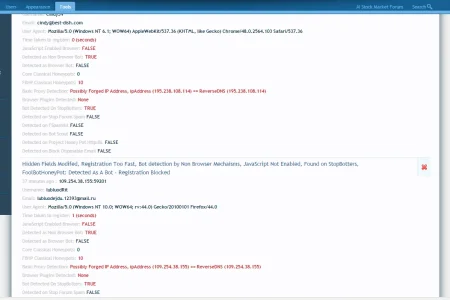
As you will see from your logs, the core honey pots are being targeted by some bots, both types of bots are getting past them (this will become more common over time)
FBHP versions of classical honey pots are still working, but this wont hold be forever
... so while we still have a chance, I'm going to pick up everything I can about these new bots to use it against them in the future
... If you ever see a bot that hits any honey pots, but does not trigger either the "non browsers bot" detection, or the "browser bot" detection methods,
I would be very interested in this type of bot... simply because I don't think it exists
There are many types of bots, I'm understanding more about each one, but some bots are fairly unique
The ones that attempt to register on forums are:
- Xrumer
- GSA
- A-Poster
- SEnuke X
- miniXrumer
- magic submitter
- buzzbundle
- Sick Submitter
- AMR
- Money Robot
- ... etc
.. to add to that list, there are custom designs (such as selenium )
So you can see there are quite a few, Xrumer and GSA are the most common and dangerous to xenforo
As far as I know, so far I think it is only Xrumer and custom designs that are js enabled
- fbhp now protects against all ... again