1966Mustang
Member
Just made a long post to my users who have not updated their passwords in years. This was done because one of my users contacted me bright and early that he received an email with his site password in the Subject line.
Supposedly the attacker was going to release videos and images of the users' pleasures to the world if he didn't cough up 10 bitcoin or whatever. Naturally, the user was concerned, so I had him forward the email with headers to me.

You can lead them to water...
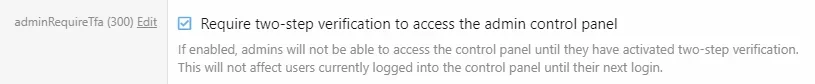
For some examples in my 'Change your damn password' post, I used the classic rockyou.txt for examples of 'this is why you need to rotate passwords and enable 2fa, rate limiting to /login, etc' there's something like +14 million examples of compromised passwords in the version I have.
One of the interesting things I discovered was that the password strength indicator does warn a bit- but there are many 'strong' passwords in rockyou.txt that the password strength declares ' This is a very strong password.' - and they are not.
I'm not proposing a table for comparing 150MB of compromised passwords to what the user enters. But we need some more password controls.
Also, if I'm 'doing' it wrong in my analysis of why this user got this email - I need to know where to look, cause I don't see a config issue in my setup. I did enable rate limiting to the /login page in my nginx config.
Any advice?
Thanks,
Supposedly the attacker was going to release videos and images of the users' pleasures to the world if he didn't cough up 10 bitcoin or whatever. Naturally, the user was concerned, so I had him forward the email with headers to me.
Code:
From: Wilkins@someattackerurlblahblah.blah
To: foo@bar.baz
Sent: 1/25/2021 3:38:30 AM Eastern Standard Time
Subject: meeeeee
...You can lead them to water...
For some examples in my 'Change your damn password' post, I used the classic rockyou.txt for examples of 'this is why you need to rotate passwords and enable 2fa, rate limiting to /login, etc' there's something like +14 million examples of compromised passwords in the version I have.
One of the interesting things I discovered was that the password strength indicator does warn a bit- but there are many 'strong' passwords in rockyou.txt that the password strength declares ' This is a very strong password.' - and they are not.
I'm not proposing a table for comparing 150MB of compromised passwords to what the user enters. But we need some more password controls.
Also, if I'm 'doing' it wrong in my analysis of why this user got this email - I need to know where to look, cause I don't see a config issue in my setup. I did enable rate limiting to the /login page in my nginx config.
Any advice?
Thanks,