Externalizable
Member
- Affected version
- XenForo 2.2.6 Patch 1
Currently, we use XenForo's built-in image proxying to protect our users from having their IP addresses collected by third parties. I'm aware that XenForo does not advertise this as a feature of image proxying, but we've been made aware of a proxy.php bypass that could benefit from being addressed even outside of security concerns.
If a user quotes a post, containing a proxied image, the reply box loads the image from its source URL. I am using this thread on xenforo.com/community (Test messages sub-forum) to verify this report.
This image Brogan linked has been proxied as expected:
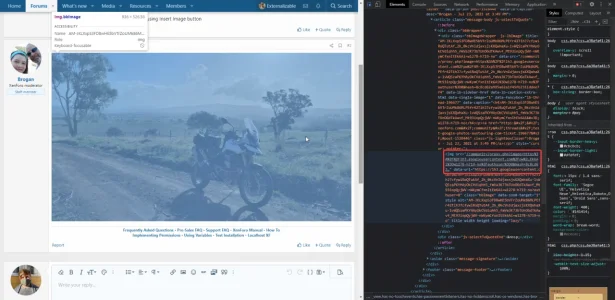
However, when I attempt to quote Brogan's post, the original image is loaded instead:
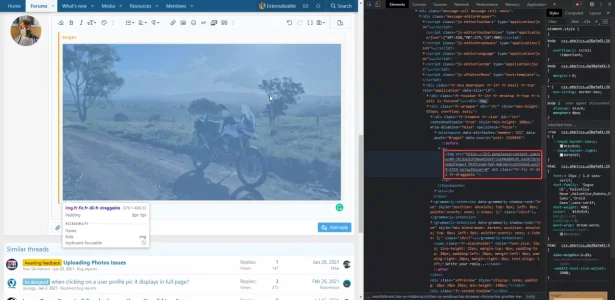
We ran an internal test, using a vanilla XenForo set-up, and can confirm that IP addresses are indeed exposed when quoting or editing a post containing a proxied image. This puts Forum moderators, who are instructed to edit posts, at risk of an attack.
If a user quotes a post, containing a proxied image, the reply box loads the image from its source URL. I am using this thread on xenforo.com/community (Test messages sub-forum) to verify this report.
This image Brogan linked has been proxied as expected:

However, when I attempt to quote Brogan's post, the original image is loaded instead:

We ran an internal test, using a vanilla XenForo set-up, and can confirm that IP addresses are indeed exposed when quoting or editing a post containing a proxied image. This puts Forum moderators, who are instructed to edit posts, at risk of an attack.
