Simon R
Member
Hi
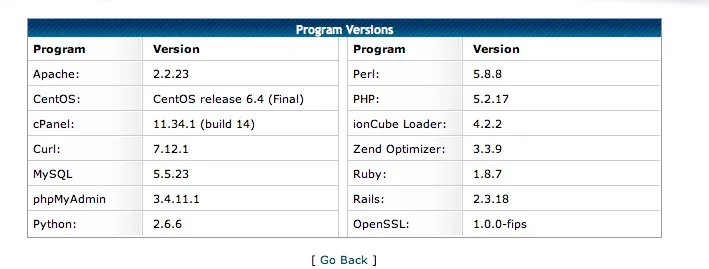
Just had the forum hacked by the people mentioned here http://www.simplemachines.org/community/index.php?topic=352040.0
I found they had somehow replaced the forum index.php file ... so I had a copy of that and replaced it but I'm getting the following errors
Any help appreciated
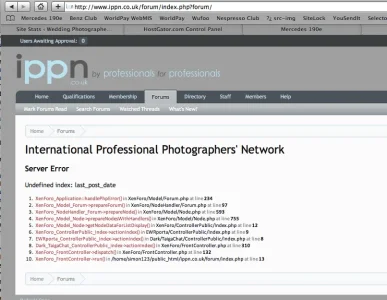
Just had the forum hacked by the people mentioned here http://www.simplemachines.org/community/index.php?topic=352040.0
I found they had somehow replaced the forum index.php file ... so I had a copy of that and replaced it but I'm getting the following errors
Any help appreciated