Not what I said. If a mail server requires a trusted TLS connection in order to send to, then Lets Encrypt (LE) will fail, as they are not considered trusted. Some Government organisations and large corporate networks often require their outgoing mail connections to only connect with TRUSTED TLS connections. Smaller organisations seem to be slowly opting only for TRUSTED TLS connections too.What documentation have you found that states that governmental entities won't accept an approved global CA issued certificate.
I would put it down to a sign of our times, more than anything.
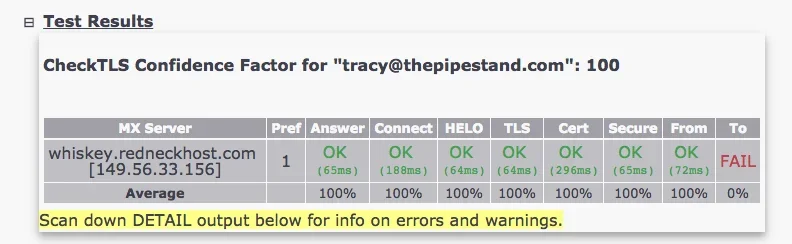
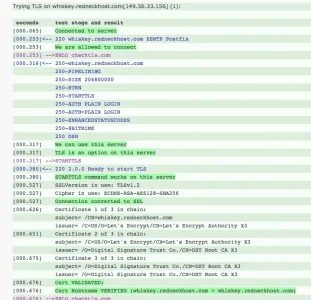
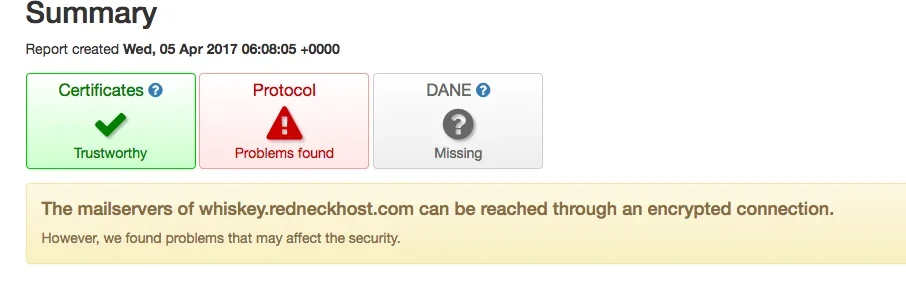
Yes, you can send with LE, you can receive too, you can establish a TLS connection for websites and such... BUT, if you want to receive mail and not bounce anyone sending to you, then LE is not the TLS you use for your mail server FQDN. It will fail validation from any org that has set their mailer to require a TRUSTED TLS connection.
Use it on your website -- DON'T USE IT ON YOUR MAIL FQDN -- not if you want to accept all email without issue.
The issue is now becoming more common -- and for business, you can't afford for current or potential customers to have their email bouncing all because you opted for a free vs $10 per annum trusted CA.
Honestly, if you ran a large website that the FQDN did a lot of mail receiving, you would have people using their work email that would likely be bouncing if your incoming FQDN is registering as untrusted connection. They've probably shifted to an online email account with less strict rules (gmail, yahoo, hotmail, etc).
Last edited: