sci_hacker
New member
- Affected version
- Firefox
Hi, XENFORO SECURITY TEAM
I'm ANTO
Vulnerability
Stored xss in (https://74bd69fab50fdc98.demo-xenforo.com/2110p2/admin.php?bb-codes).
STEPS TO REPRODUCE
Regards,
Anto
I'm ANTO
Vulnerability
Stored xss in (https://74bd69fab50fdc98.demo-xenforo.com/2110p2/admin.php?bb-codes).
STEPS TO REPRODUCE
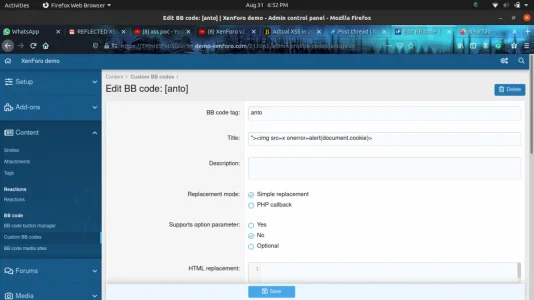
- Go to (https://74bd69fab50fdc98.demo-xenforo.com/2110p2/admin.php?bb-codes).
- Go to the add bb code and paste this payload in title "><img src=x onerror=alert(document.domain)>
- and save.
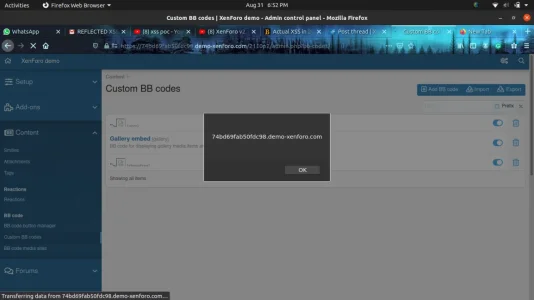
- Then see the response in the browser and the popup will appear.
Impact
With the help of XSS, a hacker or attacker can perform social engineering on users by redirecting them from real websites to fake ones. The hacker can steal their cookies and download malware on their system, and there are many more attacking scenarios a skilled attacker can perform with XSS.Regards,
Anto