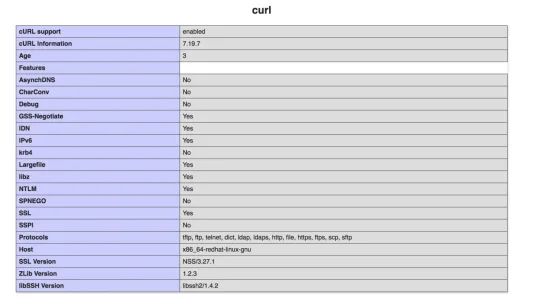
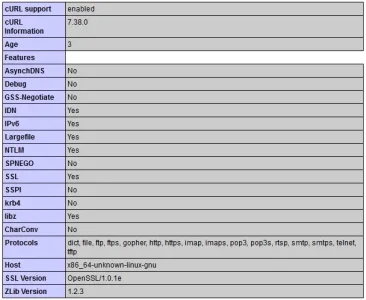
ibaker
Well-known member
- Affected version
- v2 beta 4
Just did a clean install of v2 on a spare domain for testing leaving everything basic and keep on getting a reCapture error:
Server error log
#0 src/vendor/guzzlehttp/guzzle/src/RequestFsm.php(104): GuzzleHttp\Exception\RequestException::wrapException(Object(GuzzleHttp\Message\Request), Object(GuzzleHttp\Ring\Exception\RingException)) #1 src/vendor/guzzlehttp/guzzle/src/RequestFsm.php(132): GuzzleHttp\RequestFsm->__invoke(Object(GuzzleHttp\Transaction)) #2 src/vendor/react/promise/src/FulfilledPromise.php(25): GuzzleHttp\RequestFsm->GuzzleHttp\{closure}(Array) #3 src/vendor/react/promise/src/Promise.php(119): React\Promise\FulfilledPromise->then(Object(Closure), NULL) #4 src/vendor/react/promise/src/Promise.php(166): React\Promise\Promise->React\Promise\{closure}(Object(React\Promise\FulfilledPromise)) #5 src/vendor/react/promise/src/Promise.php(133): React\Promise\Promise->settle(Object(React\Promise\FulfilledPromise)) #6 src/vendor/react/promise/src/Promise.php(201): React\Promise\Promise->resolve(Array) #7 [internal function]: React\Promise\Promise->React\Promise\{closure}(Array) #8 src/vendor/react/promise/src/Deferred.php(35): call_user_func(Object(Closure), Array) #9 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(247): React\Promise\Deferred->resolve(Array) #10 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(136): GuzzleHttp\Ring\Client\CurlMultiHandler->processMessages() #11 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Client\CurlMultiHandler->execute() #12 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Ring\Future\FutureArray->invokeWait() #13 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Future\FutureArray->wait() #14 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Message\FutureResponse->invokeWait() #15 src/vendor/guzzlehttp/guzzle/src/Client.php(176): GuzzleHttp\Message\FutureResponse->wait() #16 src/vendor/guzzlehttp/guzzle/src/Client.php(150): GuzzleHttp\Client->send(Object(GuzzleHttp\Message\Request)) #17 src/XF/Captcha/ReCaptcha.php(83): GuzzleHttp\Client->post('https://www.goo...', Array) #18 src/XF/Mvc/Controller.php(771): XF\Captcha\ReCaptcha->isValid() #19 src/XF/Pub/Controller/Register.php(344): XF\Mvc\Controller->captchaIsValid() #20 src/XF/Mvc/Dispatcher.php(249): XF\Pub\Controller\Register->actionRegister(Object(XF\Mvc\ParameterBag)) #21 src/XF/Mvc/Dispatcher.php(89): XF\Mvc\Dispatcher->dispatchClass('XF:Register', 'register', 'json', Object(XF\Mvc\ParameterBag), '', Object(XF\Pub\Controller\Register), NULL) #22 src/XF/Mvc/Dispatcher.php(41): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch)) #23 src/XF/App.php(1787): XF\Mvc\Dispatcher->run() #24 src/XF.php(326): XF\App->run() #25 index.php(13): XF::runApp('XF\\Pub\\App') #26 {main}
-------------
Previous GuzzleHttp\Ring\Exception\RingException: cURL error 60: See http://curl.haxx.se/libcurl/c/libcurl-errors.html - src/vendor/guzzlehttp/ringphp/src/Client/CurlFactory.php:127 #0 src/vendor/guzzlehttp/ringphp/src/Client/CurlFactory.php(91): GuzzleHttp\Ring\Client\CurlFactory::createErrorResponse(Object(GuzzleHttp\Ring\Client\CurlMultiHandler), Array, Array) #1 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(244): GuzzleHttp\Ring\Client\CurlFactory::createResponse(Object(GuzzleHttp\Ring\Client\CurlMultiHandler), Array, Array, Array, Resource id #111) #2 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(136): GuzzleHttp\Ring\Client\CurlMultiHandler->processMessages() #3 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Client\CurlMultiHandler->execute() #4 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Ring\Future\FutureArray->invokeWait() #5 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Future\FutureArray->wait() #6 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Message\FutureResponse->invokeWait() #7 src/vendor/guzzlehttp/guzzle/src/Client.php(176): GuzzleHttp\Message\FutureResponse->wait() #8 src/vendor/guzzlehttp/guzzle/src/Client.php(150): GuzzleHttp\Client->send(Object(GuzzleHttp\Message\Request)) #9 src/XF/Captcha/ReCaptcha.php(83): GuzzleHttp\Client->post('https://www.goo...', Array) #10 src/XF/Mvc/Controller.php(771): XF\Captcha\ReCaptcha->isValid() #11 src/XF/Pub/Controller/Register.php(344): XF\Mvc\Controller->captchaIsValid() #12 src/XF/Mvc/Dispatcher.php(249): XF\Pub\Controller\Register->actionRegister(Object(XF\Mvc\ParameterBag)) #13 src/XF/Mvc/Dispatcher.php(89): XF\Mvc\Dispatcher->dispatchClass('XF:Register', 'register', 'json', Object(XF\Mvc\ParameterBag), '', Object(XF\Pub\Controller\Register), NULL) #14 src/XF/Mvc/Dispatcher.php(41): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch)) #15 src/XF/App.php(1787): XF\Mvc\Dispatcher->run() #16 src/XF.php(326): XF\App->run() #17 index.php(13): XF::runApp('XF\\Pub\\App') #18 {main} Request state
array(4) { ["url"] => string(18) "/register/register" ["referrer"] => string(36) "http://www.xyz.com.au/register/" ["_GET"] => array(0) { } ["_POST"] => array(15) { ["username"] => string(0) "" ["146e6b59f9d10f5ede159ec21ff72a0fb32da352"] => string(7) "xxx" ["370e2347657873385931416de90624cadc6234e2"] => string(25) "xxx@outlook.com.au" ["9346ebdfbad5a836cdd08c125114b6406669b60d"] => string(8) "********" ["dob_month"] => string(1) "xx" ["dob_day"] => string(2) "xx" ["dob_year"] => string(4) "xxxx" ["location"] => string(8) "Goulburn" ["g-recaptcha-response"] => string(505) "03AJzQf7P6umdNHMX_8_RdRDZEc5d7biJcCmbM6uzMM1GKeIP7_UAV9m3LdLWTVGoyJ1D4HWfePT1rP9eM94V7ESSyapzucF6uZKCCyZeBqY8RxTDHHYuaYkex6tT264awEKzaYlN484udAtnHW6O1h5OTq1zlx3N2w1kOPy7NfUaeVtuK0r8ZsRpE3_03HK9YUgXIVG0K8GWUY0QfYjq4GtobdCnvzpNyyTgzH8A8fwWSYG_4ulN4tmE_CFt10Vt23lElAxL0SUmwGoboMW95zjM3-pA5kZ-IyBmaVtYnLP9OJTLvWa4aeTZCNyR8nM2HAWbn8GaCgXHi0OZbSZGZVijGNgT8DvFFtU0AMPez1IHXV5aKOidLc6ktamFwpecHeMRVDLEXTc336UvL4k7FlRFGXJMAUNR79LsB8q-frPK6vYadbZasnTTaGuTCmWwJ84f3G3Z0gPtb-9GNShbrDIw4eLEMY6YHfODUlovpg5Qd0008euFoCYk" ["reg_key"] => string(16) "poBQZLq3hw4lDuoI" ["fcef3adbf1fd9331ab91f9d8a747a494c7b071c9"] => string(16) "Australia/Sydney" ["_xfToken"] => string(8) "********" ["_xfRequestUri"] => string(10) "/register/" ["_xfWithData"] => string(1) "1" ["_xfResponseType"] => string(4) "json" } }
Server error log
- GuzzleHttp\Exception\RequestException: ReCAPTCHA connection error: cURL error 60: See http://curl.haxx.se/libcurl/c/libcurl-errors.html
- src/vendor/guzzlehttp/guzzle/src/Exception/RequestException.php:51
- Generated by: Unknown account
- Sep 29, 2017 at 2:16 PM
#0 src/vendor/guzzlehttp/guzzle/src/RequestFsm.php(104): GuzzleHttp\Exception\RequestException::wrapException(Object(GuzzleHttp\Message\Request), Object(GuzzleHttp\Ring\Exception\RingException)) #1 src/vendor/guzzlehttp/guzzle/src/RequestFsm.php(132): GuzzleHttp\RequestFsm->__invoke(Object(GuzzleHttp\Transaction)) #2 src/vendor/react/promise/src/FulfilledPromise.php(25): GuzzleHttp\RequestFsm->GuzzleHttp\{closure}(Array) #3 src/vendor/react/promise/src/Promise.php(119): React\Promise\FulfilledPromise->then(Object(Closure), NULL) #4 src/vendor/react/promise/src/Promise.php(166): React\Promise\Promise->React\Promise\{closure}(Object(React\Promise\FulfilledPromise)) #5 src/vendor/react/promise/src/Promise.php(133): React\Promise\Promise->settle(Object(React\Promise\FulfilledPromise)) #6 src/vendor/react/promise/src/Promise.php(201): React\Promise\Promise->resolve(Array) #7 [internal function]: React\Promise\Promise->React\Promise\{closure}(Array) #8 src/vendor/react/promise/src/Deferred.php(35): call_user_func(Object(Closure), Array) #9 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(247): React\Promise\Deferred->resolve(Array) #10 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(136): GuzzleHttp\Ring\Client\CurlMultiHandler->processMessages() #11 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Client\CurlMultiHandler->execute() #12 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Ring\Future\FutureArray->invokeWait() #13 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Future\FutureArray->wait() #14 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Message\FutureResponse->invokeWait() #15 src/vendor/guzzlehttp/guzzle/src/Client.php(176): GuzzleHttp\Message\FutureResponse->wait() #16 src/vendor/guzzlehttp/guzzle/src/Client.php(150): GuzzleHttp\Client->send(Object(GuzzleHttp\Message\Request)) #17 src/XF/Captcha/ReCaptcha.php(83): GuzzleHttp\Client->post('https://www.goo...', Array) #18 src/XF/Mvc/Controller.php(771): XF\Captcha\ReCaptcha->isValid() #19 src/XF/Pub/Controller/Register.php(344): XF\Mvc\Controller->captchaIsValid() #20 src/XF/Mvc/Dispatcher.php(249): XF\Pub\Controller\Register->actionRegister(Object(XF\Mvc\ParameterBag)) #21 src/XF/Mvc/Dispatcher.php(89): XF\Mvc\Dispatcher->dispatchClass('XF:Register', 'register', 'json', Object(XF\Mvc\ParameterBag), '', Object(XF\Pub\Controller\Register), NULL) #22 src/XF/Mvc/Dispatcher.php(41): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch)) #23 src/XF/App.php(1787): XF\Mvc\Dispatcher->run() #24 src/XF.php(326): XF\App->run() #25 index.php(13): XF::runApp('XF\\Pub\\App') #26 {main}
-------------
Previous GuzzleHttp\Ring\Exception\RingException: cURL error 60: See http://curl.haxx.se/libcurl/c/libcurl-errors.html - src/vendor/guzzlehttp/ringphp/src/Client/CurlFactory.php:127 #0 src/vendor/guzzlehttp/ringphp/src/Client/CurlFactory.php(91): GuzzleHttp\Ring\Client\CurlFactory::createErrorResponse(Object(GuzzleHttp\Ring\Client\CurlMultiHandler), Array, Array) #1 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(244): GuzzleHttp\Ring\Client\CurlFactory::createResponse(Object(GuzzleHttp\Ring\Client\CurlMultiHandler), Array, Array, Array, Resource id #111) #2 src/vendor/guzzlehttp/ringphp/src/Client/CurlMultiHandler.php(136): GuzzleHttp\Ring\Client\CurlMultiHandler->processMessages() #3 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Client\CurlMultiHandler->execute() #4 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Ring\Future\FutureArray->invokeWait() #5 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(118): GuzzleHttp\Ring\Future\FutureArray->wait() #6 src/vendor/guzzlehttp/ringphp/src/Future/BaseFutureTrait.php(55): GuzzleHttp\Message\FutureResponse->invokeWait() #7 src/vendor/guzzlehttp/guzzle/src/Client.php(176): GuzzleHttp\Message\FutureResponse->wait() #8 src/vendor/guzzlehttp/guzzle/src/Client.php(150): GuzzleHttp\Client->send(Object(GuzzleHttp\Message\Request)) #9 src/XF/Captcha/ReCaptcha.php(83): GuzzleHttp\Client->post('https://www.goo...', Array) #10 src/XF/Mvc/Controller.php(771): XF\Captcha\ReCaptcha->isValid() #11 src/XF/Pub/Controller/Register.php(344): XF\Mvc\Controller->captchaIsValid() #12 src/XF/Mvc/Dispatcher.php(249): XF\Pub\Controller\Register->actionRegister(Object(XF\Mvc\ParameterBag)) #13 src/XF/Mvc/Dispatcher.php(89): XF\Mvc\Dispatcher->dispatchClass('XF:Register', 'register', 'json', Object(XF\Mvc\ParameterBag), '', Object(XF\Pub\Controller\Register), NULL) #14 src/XF/Mvc/Dispatcher.php(41): XF\Mvc\Dispatcher->dispatchLoop(Object(XF\Mvc\RouteMatch)) #15 src/XF/App.php(1787): XF\Mvc\Dispatcher->run() #16 src/XF.php(326): XF\App->run() #17 index.php(13): XF::runApp('XF\\Pub\\App') #18 {main} Request state
array(4) { ["url"] => string(18) "/register/register" ["referrer"] => string(36) "http://www.xyz.com.au/register/" ["_GET"] => array(0) { } ["_POST"] => array(15) { ["username"] => string(0) "" ["146e6b59f9d10f5ede159ec21ff72a0fb32da352"] => string(7) "xxx" ["370e2347657873385931416de90624cadc6234e2"] => string(25) "xxx@outlook.com.au" ["9346ebdfbad5a836cdd08c125114b6406669b60d"] => string(8) "********" ["dob_month"] => string(1) "xx" ["dob_day"] => string(2) "xx" ["dob_year"] => string(4) "xxxx" ["location"] => string(8) "Goulburn" ["g-recaptcha-response"] => string(505) "03AJzQf7P6umdNHMX_8_RdRDZEc5d7biJcCmbM6uzMM1GKeIP7_UAV9m3LdLWTVGoyJ1D4HWfePT1rP9eM94V7ESSyapzucF6uZKCCyZeBqY8RxTDHHYuaYkex6tT264awEKzaYlN484udAtnHW6O1h5OTq1zlx3N2w1kOPy7NfUaeVtuK0r8ZsRpE3_03HK9YUgXIVG0K8GWUY0QfYjq4GtobdCnvzpNyyTgzH8A8fwWSYG_4ulN4tmE_CFt10Vt23lElAxL0SUmwGoboMW95zjM3-pA5kZ-IyBmaVtYnLP9OJTLvWa4aeTZCNyR8nM2HAWbn8GaCgXHi0OZbSZGZVijGNgT8DvFFtU0AMPez1IHXV5aKOidLc6ktamFwpecHeMRVDLEXTc336UvL4k7FlRFGXJMAUNR79LsB8q-frPK6vYadbZasnTTaGuTCmWwJ84f3G3Z0gPtb-9GNShbrDIw4eLEMY6YHfODUlovpg5Qd0008euFoCYk" ["reg_key"] => string(16) "poBQZLq3hw4lDuoI" ["fcef3adbf1fd9331ab91f9d8a747a494c7b071c9"] => string(16) "Australia/Sydney" ["_xfToken"] => string(8) "********" ["_xfRequestUri"] => string(10) "/register/" ["_xfWithData"] => string(1) "1" ["_xfResponseType"] => string(4) "json" } }