gldtn
Well-known member
Hello, some of my members are reporting errors when trying to edit a post and clicking on "More options". Apparently they are using chrome on windows.
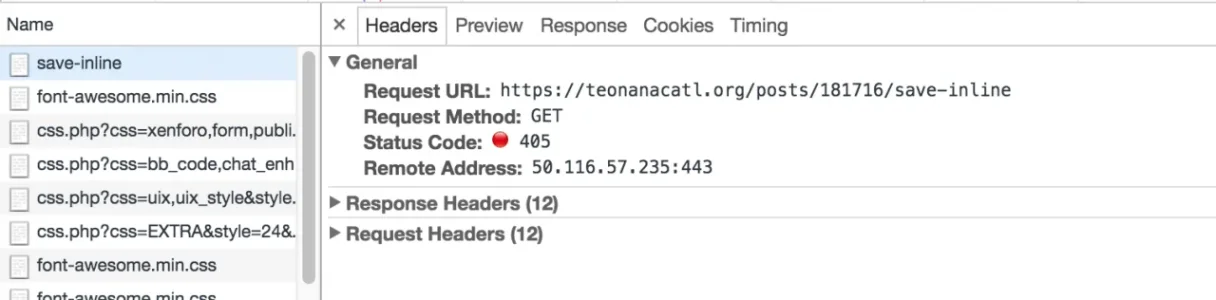
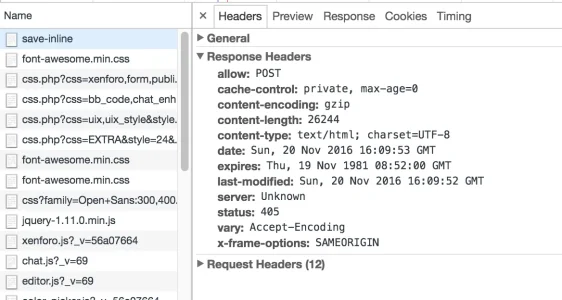
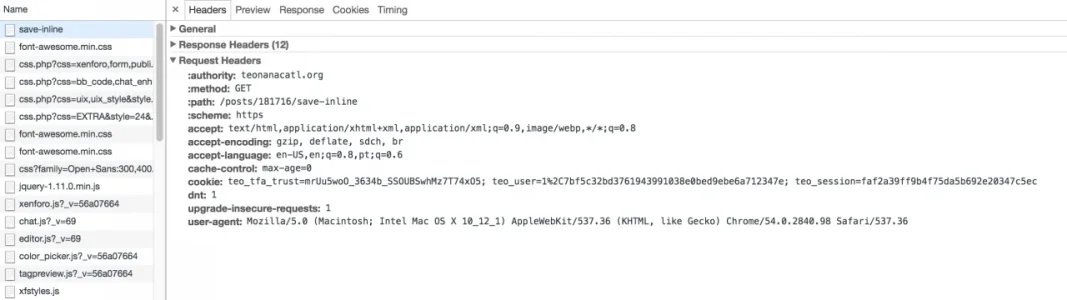
Here is some screenshot they sent me:
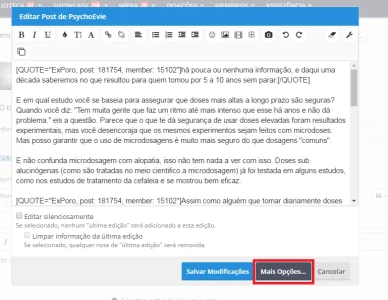
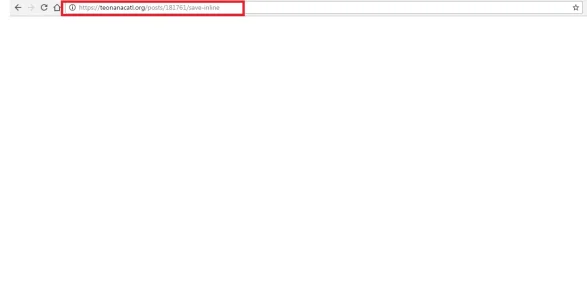
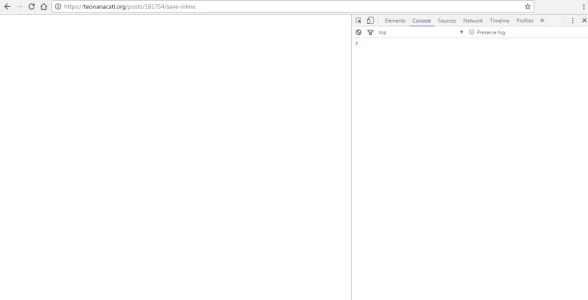
And refreshing the page it gives them a post error saying they can only perform such action "via post" and to go back and try again!
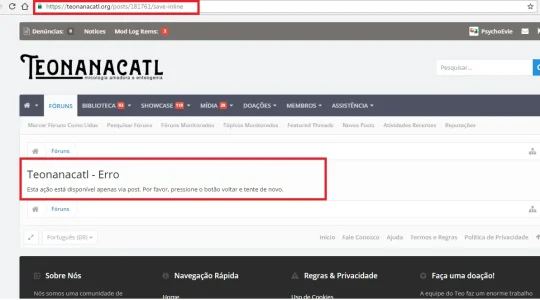
Has anything like this been reported? I tried duplicating this error, but I couldn't neither on Windows or macOS .
Thank you!
Here is some screenshot they sent me:



And refreshing the page it gives them a post error saying they can only perform such action "via post" and to go back and try again!

Has anything like this been reported? I tried duplicating this error, but I couldn't neither on Windows or macOS .
Thank you!