Sim
Well-known member
- Affected version
- 2.3.0 Beta 3 / xenforo.com
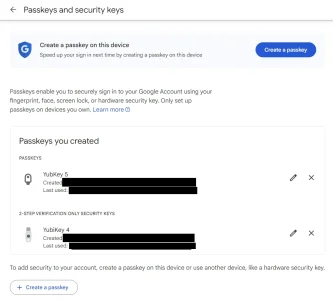
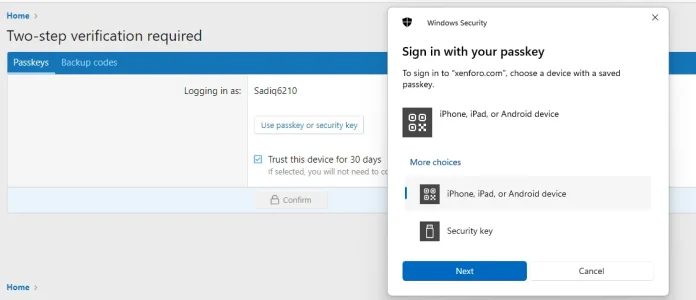
After setting up my 3 YubiKey devices as 2FA options on xenforo.com/community, none of them are working.
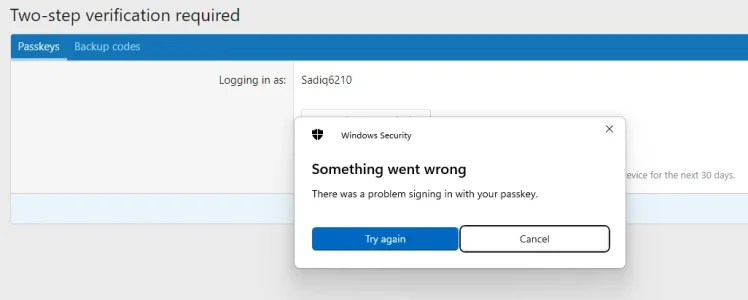
I get to the point of it asking for my PIN but then I get an error:
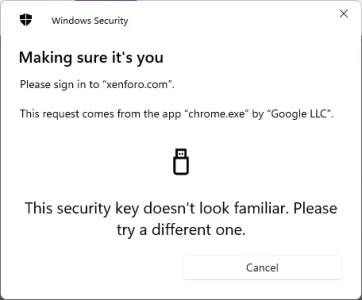
The same error occurs with all 3 devices.
I can log in using a passkey with 1Password or with Windows Hello, but none of my yubikeys are recognised.
I tried deleting and then re-adding the passkey, but I get the same result.
I get to the point of it asking for my PIN but then I get an error:

The same error occurs with all 3 devices.
I can log in using a passkey with 1Password or with Windows Hello, but none of my yubikeys are recognised.
I tried deleting and then re-adding the passkey, but I get the same result.