You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
[DigitalPoint] App for Cloudflare® 1.9.8
No permission to download
- Thread starter digitalpoint
- Start date
Hi @digitalpoint
Is it possible to enable a specific "firewall rule"
Using cmd.php, I want to auto-enable a specific firewall when I'm under DDOS attack via Linux cron or systemd timer.
Thanks for the much-needed addon for Cloudflare users.
Is it possible to enable a specific "firewall rule"
under /admin.php?cloudflare/firewall via CLI?Using cmd.php, I want to auto-enable a specific firewall when I'm under DDOS attack via Linux cron or systemd timer.
Thanks for the much-needed addon for Cloudflare users.
MentaL
Well-known member
if the remote server is overloaded then it might be best to just enable auto-ddos mitigation via the CF website directly.Hi @digitalpoint
Is it possible to enable a specific "firewall rule"under /admin.php?cloudflare/firewallvia CLI?
Using cmd.php, I want to auto-enable a specific firewall when I'm under DDOS attack via Linux cron or systemd timer.
Thanks for the much-needed addon for Cloudflare users.
Yes, that is possible only if I'm home or not sleeping.if the remote server is overloaded then it might be best to just enable auto-ddos mitigation via the CF website directly.
But sometimes attacks happen when I'm offline.
digitalpoint
Well-known member
While I’m not opposed to CLI functionality in principle, I don’t think a mechanism to enable DDoS protection from the machine being attacked is really the best idea. If it’s a real attack, cron isn’t going to function even, so… your better option is an external cron that runs on a Cloudflare Worker or something so it’s decoupled from the server being attacked.
While using Cloudflare, the attacker can only launch Layer 7/application attacks.
The server mostly is functional even with large attacks; it's PHP-FPM/MariaDB that would most likely be kaput or start to respond so slowly.
Other Linux services still work fine, including cron.
But if it can be detected early on, like detecting server load or port 443 connections reaching a certain unexpected amount, it can be prevented from overloading the server.
 .
.
The server mostly is functional even with large attacks; it's PHP-FPM/MariaDB that would most likely be kaput or start to respond so slowly.
Other Linux services still work fine, including cron.
But if it can be detected early on, like detecting server load or port 443 connections reaching a certain unexpected amount, it can be prevented from overloading the server.
This is a much better way, relying on an external server, but I'm not sure yet how to implement thisyour better option is an external cron that runs on a Cloudflare Worker or something so it’s decoupled from the server being attacked.
digitalpoint
Well-known member
Depends on how strong the attack is. I’ve dealt with attacks strong enough that the kernel itself would crash and the operating system just ceased to function (the OS could launch any new processes, including cron). If your server’s cron still functions, it’s a weak sauce attack. 
MentaL
Well-known member
Depends on how strong the attack is. I’ve dealt with attacks strong enough that the kernel itself would crash and the operating system just ceased to function (the OS could launch any new processes, including cron). If your server’s cron still functions, it’s a weak sauce attack.
all you need is to overload bandwidth and hit a good ol' bottleneck. Unless you got some sort of KVM access somewhere, that's enough to ruin a lot of fun.
digitalpoint
Well-known member
Are you actually getting attacks that Cloudflare isn’t automatically mitigating? I’m curious what sort of firewall rule you are needing to enable that is doing a better job of DDoS protection than Cloudflare is doing. Would is make sense to just have that rules enabled all the time?
Some of the HTTP floods aren't detected by Cloudflare and hit directly my origin server (this happens a lot).Are you actually getting attacks that Cloudflare isn’t automatically mitigating?
Sometimes Cloudflare DDoS protection detects only after a few minutes, bringing the server down.
Sometimes the attack is not considered a threat by Cloudflare because they are using 300k+ unique IPs at once but only 5-10 connections per IP every few seconds but still bringing my server down.
It's similar to the "I'm under attack mode," but I apologize; I won't post specific details here because my forum competitors are also lurkers on this forum.I’m curious what sort of firewall rule you are needing to enable that is doing a better job of DDoS protection than Cloudflare is doing.
Based on experience, Cloudflare DDoS protection isn't tailored much for PHP web apps.Cloudflare is doing
The attackers know which specific Xenforo pages are heavy on the PHP/MariaDB side and vulnerable to HTTPS flood attacks.
But it could block some SEO bots and also interfere with legitimate users.Would is make sense to just have that rules enabled all the time?
Ivancas
Well-known member
@digitalpoint when I try to edit a banner ad from Siropu Ads Manager I get the following error:Sort of... XenForo uses an abstract filesystem fordataandinternal_data. Data is intended to be public (things like avatars and attachment previews are direct requests for the public URL. Things in internal_data are intended to be private (not publicly accessible... things like full attachments) so that the application can do permission checks and choose to serve (or not) the content based on those permissions. All of that is generally how XenForo works (with or without R2).
By default, XenForo uses a local file system adapter for the abstracted file system (it never reads or writes directly to the folders, rather it reads and writes to the local filesystem adapter for the abstracted file system). That's why you can just plug in alternate filesystems fairly easily.
Hopefully that makes it a little more clear how the underpinnings of XenForo work. And to answer your question about where a private (internal_data) file is stored when it's read from an abstracted file system, it's not stored anywhere other than in server memory for that single request. There is no cache or temporary image created... if you were just caching everything locally, it would more or less defeat the purpose of offloading to R2.
As far as publicly accessible areas (things in the data directory), they become publicly accessible on a sub-domain so that R2/Cloudflare can serve them directly.
For example, the avatar for a user on iolabs.io (if you were using the default local filesystem adapter) would be:
With R2 it's this:
data.iolabs.io isn't on my server, it's simply handled by Cloudflare directly.
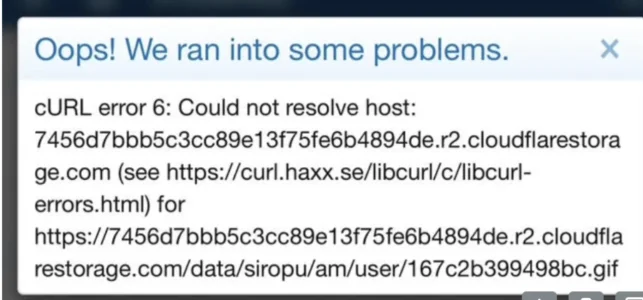
Siropu confirmed he is using the copyFileToAbstractedPath method to store the attachments. Could that be the reason why I get this R2 error?
digitalpoint
Well-known member
Looks like a DNS issue to me (DNS server that your server is using).@digitalpoint when I try to edit a banner ad from Siropu Ads Manager I get the following error:
View attachment 320905
Siropu confirmed he is using the copyFileToAbstractedPath method to store the attachments. Could that be the reason why I get this R2 error?
MentaL
Well-known member
Some of the HTTP floods aren't detected by Cloudflare and hit directly my origin server (this happens a lot).
Sometimes Cloudflare DDoS protection detects only after a few minutes, bringing the server down.
Sometimes the attack is not considered a threat by Cloudflare because they are using 300k+ unique IPs at once but only 5-10 connections per IP every few seconds but still bringing my server down.
It's similar to the "I'm under attack mode," but I apologize; I won't post specific details here because my forum competitors are also lurkers on this forum.
Based on experience, Cloudflare DDoS protection isn't tailored much for PHP web apps.
The attackers know which specific Xenforo pages are heavy on the PHP/MariaDB side and vulnerable to HTTPS flood attacks.
But it could block some SEO bots and also interfere with legitimate users.
If your serving static cached pages to guests then the impact should be minimal. What if they are attacking the source ip, bypassing CF altogether?
XFA
Well-known member
Hi,
I have an add-on of mine which uses icons that are located in data/xfa/customusernameicons/icons.
In my code I have the following:
When using default XenForo setup, the listContents output is fine.
However, for that particular user, he is using a CDN for data and the output of the listContents is empty.
I narrowed down and the listContents output is only fine if I set the second parameter to true which is from my understanding supposed to tell the function to go through the directory structure (e.g. if it had subfolders) which is not what I would want so I believe something is incorrect here, unless I misunderstood something.
Clément
I have an add-on of mine which uses icons that are located in data/xfa/customusernameicons/icons.
In my code I have the following:
PHP:
if (\XF::fs()->has('data://xfa/customusernameicons/icons'))
{
$iconsDataRaw = \XF::fs()->listContents('data://xfa/customusernameicons/icons', false);When using default XenForo setup, the listContents output is fine.
However, for that particular user, he is using a CDN for data and the output of the listContents is empty.
I narrowed down and the listContents output is only fine if I set the second parameter to true which is from my understanding supposed to tell the function to go through the directory structure (e.g. if it had subfolders) which is not what I would want so I believe something is incorrect here, unless I misunderstood something.
Clément
digitalpoint
Well-known member
R2 and other CDNs don’t have the ability to list a “directory”.Hi,
I have an add-on of mine which uses icons that are located in data/xfa/customusernameicons/icons.
In my code I have the following:
PHP:if (\XF::fs()->has('data://xfa/customusernameicons/icons')) { $iconsDataRaw = \XF::fs()->listContents('data://xfa/customusernameicons/icons', false);
When using default XenForo setup, the listContents output is fine.
However, for that particular user, he is using a CDN for data and the output of the listContents is empty.
I narrowed down and the listContents output is only fine if I set the second parameter to true which is from my understanding supposed to tell the function to go through the directory structure (e.g. if it had subfolders) which is not what I would want so I believe something is incorrect here, unless I misunderstood something.
Clément
digitalpoint
Well-known member
Ya, definitely not ideal… but that’s why listContents() can’t work in those scenarios.Ok good to know, at least as this directory should not contain a directory I'll work it that way with the recursivity.
Thank you.
digitalpoint
Well-known member
It is… that just shows you what’s free.
securedme
Well-known member
It is… that just shows you what’s free.
So after the free 10GB, the cost would be very low that I can put all attachments, pictures and even videos on the forums without worrying my wallet?
Similar threads
- Replies
- 12
- Views
- 1K