Joe Link
Well-known member
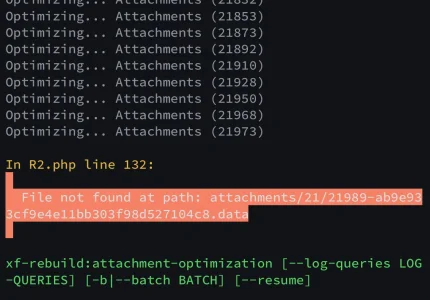
Did Cloudflare resolve their HTTP/2 to origin bug that can cause 520 errors?

Suddenly tons of CF 520 errors
Hello everybody, since yesterday afternoon there are 520 error messages from Cloudflare in our forum. The error occurs completely randomly and everywhere. We only moved to a new server a few weeks ago and everything went perfectly. I will of course also contact my hoster. But I have already...xenforo.com
They have not.
@MattW just moved us to a new VPS running Alma/CloudLinux/cPanel/Apache. We had to disable HTTP/2 to Origin due to this.