As well as every software will leak IP addresses if it does access external resources (like things like fetching images, fetching web page previews or meta data, etc.) without using a VPN or Proxy.Every forum software will leak IP addresses if you just use SMTP to send mail - this is not something unique to XenForo, it's a fundamental part of how SMTP works.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
ddos attacked on my forum any solution?
- Thread starter questlot
- Start date
-
- Tags
- ddos attack
questlot
Active member
Thanks for the opinion. Aside IP address getting leaked via email is there any means IP can get leaked? Because someone told me about IP getting leak on images.Every forum software will leak IP addresses if you just use SMTP to send mail - this is not something unique to XenForo, it's a fundamental part of how SMTP works.
questlot
Active member
Does that mean if I use myforum@gmail.com to send email IP of the forum won’t get leak again through other means?As well as every software will leak IP addresses if it does access external resources (like things like fetching images, fetching web page previews or meta data, etc.) without using a VPN or Proxy.
MySiteGuy
Well-known member
Thanks for the opinion. Aside IP address getting leaked via email is there any means IP can get leaked? Because someone told me about IP getting leak on images.
Turn off URL unfurl and the image proxy in XF.
questlot
Active member
How do i turn off the unfurl where is it located.Turn off URL unfurl and the image proxy in XF.
whynot
Well-known member
ACP > Options > MessagesHow do i turn off the unfurl where is it located.
questlot
Active member
ThanksACP > Options > Messages
questlot
Active member
@eva2000 Please tell me the step to hide ip address on image and link proxy?Xenforo’s image and link proxy Options - XenForo 2 Manual can reveal your server real IP by default unless you configure a separate server forward HTTP proxy and set it in Xenforo config file $config['http']['proxy'] Config.php options - XenForo 2 Manual
That’s what I do for my Xenforo forums. You can see discussion at XF 1.5 - Untrusted Http Client | Page 3 | XenForo community
eva2000
Well-known member
Best to read XF 1.5 - Untrusted Http Client | Page 3 | XenForo community. You’d need to get a separate second server i.e. VPS - I usually go with VPS provider with DDOS protection support and install on that second VPS a forward HTTP proxy like tinyproxy or 3proxy and configure them. Then update Xenforo config to point to that configured 2nd server’s IP in proxy setting as outlined in Xenforo thread link.@eva2000 Please tell me the step to hide ip address on image and link proxy?
motowebmaster
Well-known member
Try setting your firewall to allow your IP, and remove (or block) all ports - which would block everyone else but you. If you installed CSF as previously suggested, it can support this.
Then look at your firewall logs, and your site performance. If your VPS resources aren't over-utilized and your site is still sluggish, then I'd check to see if your website files are correct. If your site performance returns to normal, then consider sharing what your're seeing in your firewall logs with your hosting provider or someone here you trust.
Most of the DDOS attacks I've experienced were done at assets in front of my site, meaning my CPU would be very low but the site was non-responsive. Usually an attack on a front-end proxy (as eva2000 suggested) or firewall. When I blocked everyone in that scenario, it didn't yield any difference, my site was still non-responsive and CPU was still low. One event happened when I was hosting with Softlayer (the original company) and in those days they had to move me to a temporary DDOS solution and left me there for 48 hours for the attack to subside. Today several hosting providers provide real-time DDOS protection, which others have suggested in this thread, and has helped me.
The one INTRUSION I experienced changed files on my site, before I was using XF, resulted in a nearly non-responsive site and high server utilization. In that scenario, it wasn't a DDOS, the attackers used a vulnerability to write files and database records. When I blocked everyone but myself, I could access my site but the server was still at high utilization, I knew to look interally. Eventually found the changed files, and the added database records, but chose to dump all files and database and restore them both from the previous day's backup - didn't trust the 12 Hour backup. The attackers used an automated script to give them an admin account, that I couldn't see in the admin interface, but could remediate after restoring the backup. The site ran clean for two years afterward, until I migrated to a new forum software platform.
I don't use Cloudflare on my XF site, but you should consider sticking with it:
Then look at your firewall logs, and your site performance. If your VPS resources aren't over-utilized and your site is still sluggish, then I'd check to see if your website files are correct. If your site performance returns to normal, then consider sharing what your're seeing in your firewall logs with your hosting provider or someone here you trust.
Most of the DDOS attacks I've experienced were done at assets in front of my site, meaning my CPU would be very low but the site was non-responsive. Usually an attack on a front-end proxy (as eva2000 suggested) or firewall. When I blocked everyone in that scenario, it didn't yield any difference, my site was still non-responsive and CPU was still low. One event happened when I was hosting with Softlayer (the original company) and in those days they had to move me to a temporary DDOS solution and left me there for 48 hours for the attack to subside. Today several hosting providers provide real-time DDOS protection, which others have suggested in this thread, and has helped me.
The one INTRUSION I experienced changed files on my site, before I was using XF, resulted in a nearly non-responsive site and high server utilization. In that scenario, it wasn't a DDOS, the attackers used a vulnerability to write files and database records. When I blocked everyone but myself, I could access my site but the server was still at high utilization, I knew to look interally. Eventually found the changed files, and the added database records, but chose to dump all files and database and restore them both from the previous day's backup - didn't trust the 12 Hour backup. The attackers used an automated script to give them an admin account, that I couldn't see in the admin interface, but could remediate after restoring the backup. The site ran clean for two years afterward, until I migrated to a new forum software platform.
I don't use Cloudflare on my XF site, but you should consider sticking with it:
- Cloudflare - I'd setup with a free version at first so that you can get it working properly, then upgrade it to paid the options suggested in this thread.
- Hosting Provider's Firewall - Open only the ports you need, allow only from your IP and Cloudflare, preferably a provider that offers DDOS Protection.
- Firewall on your VPS - Run CSF to automatically track/block bad actors and invalid useragents, allow only from your IP and Cloudflare however your hosting provider's network is setup. If one looks at the robots listed on my XF Members/Visitors page, you would see moderately-reputable agents like Google Adsense, Bing, Google, Amazon, and etc. As of this posting there are 99 bad useragents being blocked for a week from particular countries, hacked servers, hacked PCs, and other servers within my own hosting company's data center.
Sim
Well-known member
Did you ever fix this? What was the solution?
The solution to DDOS attacks has been well covered by this thread already.
- set up Cloudflare
- prevent IP address leakage from SMTP, image proxy and unfurling
- Use an SMTP service which doesn't leak IP address, or one which sends email via API rather than by SMTP
- Implement a reverse proxy server to mask your outgoing IP address for image proxy and unfurling
- Check for any other features added by 3rd party addons which make external calls that are able to be manipulated by users on your forum to reveal your server IP address for further attacks
- change the IP address of your server
Step 3 is the most important - implementing Cloudflare and anything else you do will be pointless if you don't change the IP address of your server once everything else is set up.
fly
Well-known member
For #2, I always just added the CF IPs as the only ones that could connect to the ELB. Obviously AWS specific, but would work for other providers that have a firewall that sits in front of your network.The solution to DDOS attacks has been well covered by this thread already.
Step 2 preventing IP address leakage is the tricky one - this requires some effort and some decisions about how you manage your site. If it's just a random attack and you're not being targeted by a malicious party - then it's less important, step 1 and 3 will do the job. But if someone with knowledge of how these things work is targeting you, you'll need to be really careful with preventing IP address leakage, since it is very easy for someone to make posts on your site which will reveal your IP address via an external website that they control if you haven't taken steps to prevent it.
- set up Cloudflare
- prevent IP address leakage from SMTP, image proxy and unfurling
- Use an SMTP service which doesn't leak IP address, or one which sends email via API rather than by SMTP
- Implement a reverse proxy server to mask your outgoing IP address for image proxy and unfurling
- Check for any other features added by 3rd party addons which make external calls that are able to be manipulated by users on your forum to reveal your server IP address for further attacks
- change the IP address of your server
Step 3 is the most important - implementing Cloudflare and anything else you do will be pointless if you don't change the IP address of your server once everything else is set up.
Simply GEO Block Asia, as i can see on your screenshot its mostly ASIA IP's which indicate the DDoser using a Stresser/Booter which uses Asia Proxies.I got ddos attacked on my shared hosting and my website was taking down by Namecheap and they recommended i move to another hosting service or upgrade to a VPS plan which i did and after few hours the ddos attack begin again and namecheap support have not been able to provide any tangible solution to get the problem resolve. I have been on this issue for more than 48 hours. I have also subscribed to Cloudflare pro to see how cloudefare can block the attack. I suspect most of the attack is coming from Get, Connect, Post. Though i have little knowledge about such,
Please can anyone suggest or recommend the best solution to stop the ddos attack?
View attachment 259526
View attachment 259527
Everything else depents on the Attack and your Forum, you can work with Ratelimiting aswell.
On CF Pro you can use CF to Detect Layer 7 Attacks also.
Options like Image Proxy and so one from Xenforo can leak your IP Adress.
Same for all Email Traffic.
Opus X
Well-known member
from what my tech support guy told me not true if configured.Options like Image Proxy and so one from Xenforo can leak your IP Adress.
he recommends using digital points cloud flare add on and enabling a feature that protects it.
MentaL
Well-known member
Litespeed also helps very well on L7 based attacks coupled with CF as well. Youll need to configure it tight but for repeat concurrent connections, it works well. Also useful if someone gains your source IP and bypasses CF to hammer your webserver.
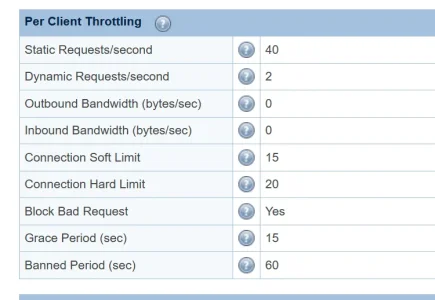
just add CF to access control
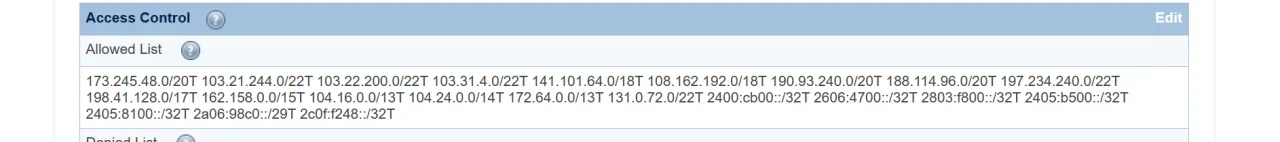

just add CF to access control
Code:
173.245.48.0/20T
103.21.244.0/22T
103.22.200.0/22T
103.31.4.0/22T
141.101.64.0/18T
108.162.192.0/18T
190.93.240.0/20T
188.114.96.0/20T
197.234.240.0/22T
198.41.128.0/17T
162.158.0.0/15T
104.16.0.0/13T
104.24.0.0/14T
172.64.0.0/13T
131.0.72.0/22T
2400:cb00::/32T
2606:4700::/32T
2803:f800::/32T
2405:b500::/32T
2405:8100::/32T
2a06:98c0::/29T
2c0f:f248::/32T
MentaL
Well-known member
SMTP can leak too in the headers. Amazon SES removes this. Any remote embedding of an image can gain as well but using image workers on CF via @digitalpoint 's addon works well. Automated and out of the box.from what my tech support guy told me not true if configured.
he recommends using digital points cloud flare add on and enabling a feature that protects it.
Opus X
Well-known member
i was told only smtp from your server.SMTP can leak too in the headers. Amazon SES removes this
he said if i use a third party smtp server it does not since their info is on it.
are you saying that is not right?
MentaL
Well-known member
it'll be down to the server configuration if it includes the source ip within the header. Amazon SES does not include it. Another way around it is by using a custom configured mail server and removing it yourself. Remote IP Loggers via image embed can leak source ip too but as I said, DP's worker mod stops that.i was told only smtp from your server.
he said if i use a third party smtp server it does not since their info is on it.
are you saying that is not right?
Similar threads
- Replies
- 24
- Views
- 586
- Replies
- 11
- Views
- 172
- Question
- Replies
- 21
- Views
- 1K