If you want to use that feature, yes, you would need to toggle it on. If you don’t want to use it, leave it off.
Why would people choose not enabling them? That is, what are the disadvantages?
If you want to use that feature, yes, you would need to toggle it on. If you don’t want to use it, leave it off.
If they didn’t want to use a proxy?Why would people choose not enabling them? That is, what are the disadvantages?
You mean there are people who don't mind having their IP exposed to the world?If they didn’t want to use a proxy?
To me this was never an XF issue but a server issue, since I had to do this fix back when I was on vB.Also before I go to sleep, does xf still have issues resolving visitors IP's from cloudflare? Or did XF push a fix for this? If not what is needed?

Using Cloudflare with various forums
Many widely used forum platforms are compatible with Cloudflare.developers.cloudflare.com

Cloudflare should continue working even with an expired cert because you have the option to tell it not to care about the expiration, just cares that the connection is encrypted.Still going well, but the larger forum I admin is hosted at a larger managed server, where we don't have root access. Our LetsEncrypt certificates expired and made a mess out of everything. Unfortunately they don't accept outside certs (although since I've been there nearly 24 years, they probably could be convinced--they instead want you to buy their certificates), but I don't know what is different about their setup vs. my other sites which are unmanaged (both run on Apache), as mine update every 60 days like clockwork. And both are behind Cloudflare. I had to disable the proxies for the sites on the managed server, get support to manually update the certificates (as they were using it on some sort of cron job once an hour), then reenable the proxy.
We might just move the managed instance over here to XF Cloud, once we can afford it. I could run the forum myself hosted at an unmanaged server (and I do for numerous other sites) but, since I'm not always available 24/7, and it is a very busy and active site, the owner wants that safety net. It's busy enough that if issues happen, they happen fast, and happen large. (Thing is, I'm probably taking on another job where I'll be nowhere near a computer, plus, I travel where I'm away from a computer for days at a time. I can see his point.)
I guess we'll see how it plays out. Main thing is, the expired certificates caused us a lot of grief with Cloudflare in the mix. I'm going to be digging in to see if I can find a way to fix this, while we decide what to do host-wise.
Cloudflare works with an expired cert, but our server doesn't. That's a problem with the host, not us.Cloudflare should continue working even with an expired cert because you have the option to tell it not to care about the expiration, just cares that the connection is encrypted.
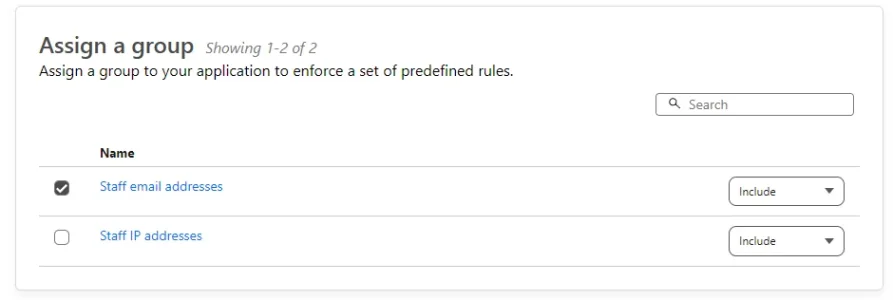
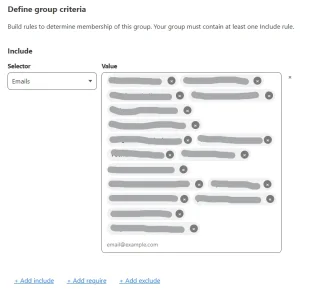
I agree, there is something letting access through. I have only a single rule for this subdomain, and I'm not seeing why it won't work using a "clean" browser and a VPN (to rule out anything stored in a browser).I'd say it's fairly safe to say that your Zero Trust Access rule is either not matching the request, or you have a different rule taking priority that is letting it through.
Yeah, that's what I'm thinking also.Well, what I would do is simplify everything and slowly add individual things until you fnid the culprit. Like start with blocking test.yourdomain.com/zero-trust-test for everyone. Check if that works as intended, if it does add one more thing... like allowing one user to access it. Check that... etc, etc...
You will find which exact part is causing an issue as you add one thing at a time.
I realized that I had to set the test subdomain to "Proxy" rather than "DNS only" in DNS settings. I changed the setting yesterday and now it seems to be working.You will find which exact part is causing an issue as you add one thing at a time.
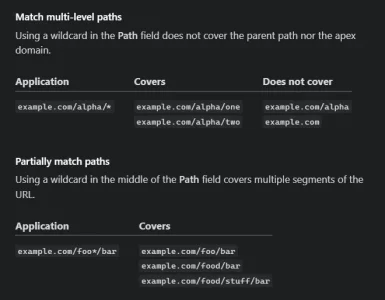
index.php, admin.php and install as paths, and those are all protected now.Any pointer to configure to configure this?Use Workers for your image proxy and URL proxy (doing this will give you a high-performance/free way to hide your server's IP address when it makes a request for images or URLs).
Easiest way is to use the App for Cloudflare addon and enable the option under Proxies.Any pointer to configure to configure this?
Thanks for the tutorial.
We use essential cookies to make this site work, and optional cookies to enhance your experience.