PaulB
Well-known member
- Affected version
- 2.2.5
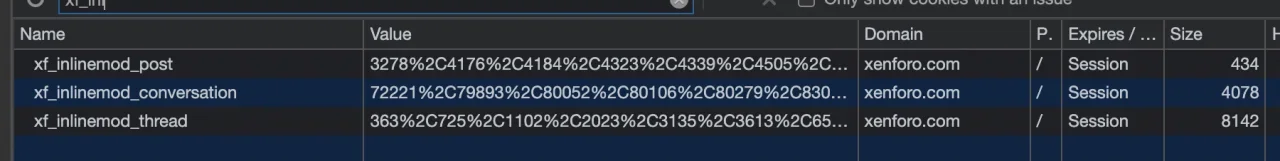
The inlinemod cookies, such as
xf_inlinemod_conversations, currently have an unbounded size. Cookies aren't really supposed to be > 4 KiB, but it's not too difficult for an end user to end up with a cookie far larger than that just by selecting several pages of conversations for deletion. From that point forward, they're likely to run into 400 errors such as the following:If you take a look at the bottom, that isn't coming from my server; it's coming from Cloudflare, so it isn't something that I can configure. This wouldn't be a huge issue if it could only be encountered by staff, but since users have access to inlinemod functionality in conversations, it poses a problem. They're not likely to realize they need to clear their cookies to continue using the site.400 Bad Request
Request Header Or Cookie Too Large
cloudflare-nginx