Feel free to Donate. Originally this was a paid add-on, but it's suspected this might now be being exploited. I've made this free so it's available to everyone (it's free for those who can't afford to donate, any amount for those that can  )
)
User locks on login attempts
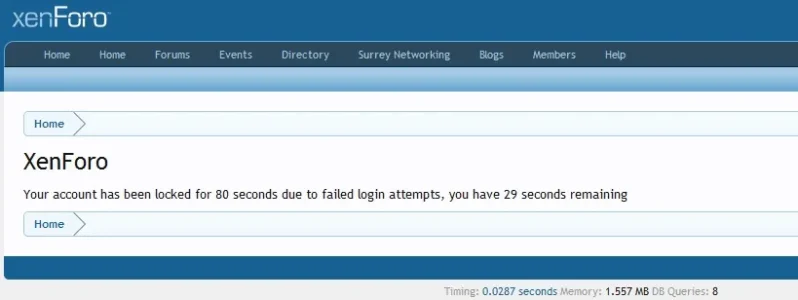
- Note, the time of the user locks is taken from the first failed attempt
There is no intention to fix this out side of XenForo 1.2 release since it has not been deemed a high enough priority security risk
This plugin fixes the following issue:
Scenario: Brute forcing the admin account is simple (and very simple under certain scenarios)
Since the Admin username is very exposed in forums, (in most cases, you can just look here: xenforo/index.php?members/.1/) it is essential that the Admin passwords are not easily brute forced
Brute force attacks are usually only possible if multiple requests can be sent very quickly
Brute forcing the Admin Control Panel area is prevented by a user lock (after about 5 attempts, the user is locked out from further attempts for about 15 minutes) this is a good measure and prevents users from gaining the password (it could take years even if only 5 attempts per 30 seconds are allowed)
However, it is possible to brute force from the front end area and gain the password that way (there are no user locks on the forum front: xenforo/index.php?login/login)
If the user has CAPTCHA in place, after 5 attempts the CAPTCHA is activated. However, this is of no use, and does not prevent multiple requests from continuing (see norecaptcha / recaptchaocr / captchasniper / AutoCaptcha / deathbycaptcha / Stiltwalker / Custom OCR / ANNs)
If QAs are set in place, the attacker only needs to log the QA questions and answers
If there are no CAPTCHA set in place, the attacker can continue brute forcing the admin user account without issue
Variations of this scenario:
1) The user uses a QA CAPTCHA, the attacker goes through the list of QAs on the forum and logs the answers, then sends the appropriate answers with their attack application (QA is rendered useless when a forum is targeted)
2) The user uses ReCapacha, the attacker can by-pass ReCaptcha
(it is even evident that this is easy to bypass due to the amount of spam on XF)
ReCaptcha is currently useless, regardless if a forum is targeted or not
3) No CAPTCHA is set in place
The attacker can brute force the admin account from the front end with a very simple script
Expected: User Locks are provided site wide for log-in attempts (especially for the Admin Accounts / Moderators Account)
Actual: User locks are only provided in the ACP area for the admin account, allowing users to brute force the Admin account and gain the Admin password from other login areas (with a very basic script)
Installation:
http:// www. yourforum.com/library/LoginUserLocks
User locks on login attempts
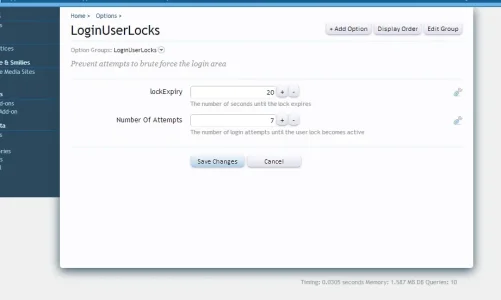
- The number of attempts until the lock kicks in is defined in the ACP
- The amount of time until the lock expires is defined in the ACP
- On locking, the user is displayed how long they must wait until the lock is released (a dynamic count down is displayed)


- Note, the time of the user locks is taken from the first failed attempt
There is no intention to fix this out side of XenForo 1.2 release since it has not been deemed a high enough priority security risk
This plugin fixes the following issue:
Scenario: Brute forcing the admin account is simple (and very simple under certain scenarios)
Since the Admin username is very exposed in forums, (in most cases, you can just look here: xenforo/index.php?members/.1/) it is essential that the Admin passwords are not easily brute forced
Brute force attacks are usually only possible if multiple requests can be sent very quickly
Brute forcing the Admin Control Panel area is prevented by a user lock (after about 5 attempts, the user is locked out from further attempts for about 15 minutes) this is a good measure and prevents users from gaining the password (it could take years even if only 5 attempts per 30 seconds are allowed)
However, it is possible to brute force from the front end area and gain the password that way (there are no user locks on the forum front: xenforo/index.php?login/login)
If the user has CAPTCHA in place, after 5 attempts the CAPTCHA is activated. However, this is of no use, and does not prevent multiple requests from continuing (see norecaptcha / recaptchaocr / captchasniper / AutoCaptcha / deathbycaptcha / Stiltwalker / Custom OCR / ANNs)
If QAs are set in place, the attacker only needs to log the QA questions and answers
If there are no CAPTCHA set in place, the attacker can continue brute forcing the admin user account without issue
Variations of this scenario:
1) The user uses a QA CAPTCHA, the attacker goes through the list of QAs on the forum and logs the answers, then sends the appropriate answers with their attack application (QA is rendered useless when a forum is targeted)
2) The user uses ReCapacha, the attacker can by-pass ReCaptcha
(it is even evident that this is easy to bypass due to the amount of spam on XF)
ReCaptcha is currently useless, regardless if a forum is targeted or not
3) No CAPTCHA is set in place
The attacker can brute force the admin account from the front end with a very simple script
Expected: User Locks are provided site wide for log-in attempts (especially for the Admin Accounts / Moderators Account)
Actual: User locks are only provided in the ACP area for the admin account, allowing users to brute force the Admin account and gain the Admin password from other login areas (with a very basic script)
Installation:
Purchase the plug-in here:http://www.surreyforum.co.uk/account/upgrades- Download the latest version (now above):
- Unzip the file
- Upload this folder into the library folder of your XenForo root
http:// www. yourforum.com/library/LoginUserLocks
- Go to ACP -> Add-ons -> Install Add-on -> Install from file on server
- Install from file on server: " library/LoginUserLocks/addon-LoginUserLocks.xml"
- Set options in the administration control panel ACP>>Home>>Options>>LoginUserLocks