@Osman After using this addon for a week I have to say I am very pleased with it once the initial hickups have been solved very quickly. I've migrated my exiting setup from .htaccess to Threat Monitor for the most part as it enables better logging and debugging along with way better options for the parts that I migrated. Maintainance is quick and easy, I've managed to lock out scrapers and resident proxies for the most part and I love the fact, that logg in users stay untouched. Brillant! I think however I found some bugs, have a bunch of questions and some suggestions for improvements.
Bugs / strange behavior first:
 1. Threat monitor misses a beat from time to time
1. Threat monitor misses a beat from time to time
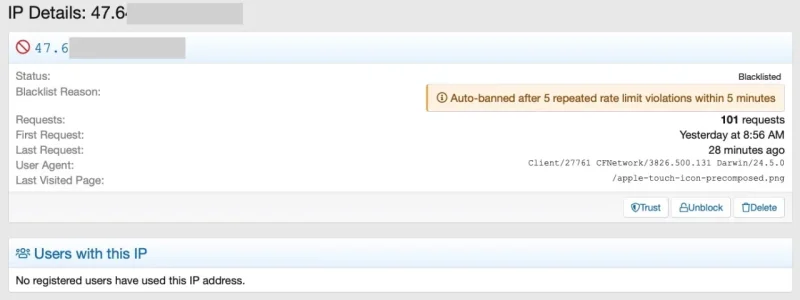
I do use country blocking (currently ~75 countries) along with ASN blocking (currently ~320 ASNs) and the general settings. Rate limiting has never been hit until now, most blocks result from country blocking and work nicely most of the time. Not using Cloudflare. However: I do use the Access Log add on from AndyB which gives me conveniently the option to check if someone is slipping through that I'd rather block and enables me to adjust my settings in Thrreat Monitor. It turned out that every now and then IPs that have been blocked by either country or ASN get through unnoticed. These affects a lot of ASNs from the us (no country block there) but also some IPs from China. As an example I found this in the access log of Andy's add on:
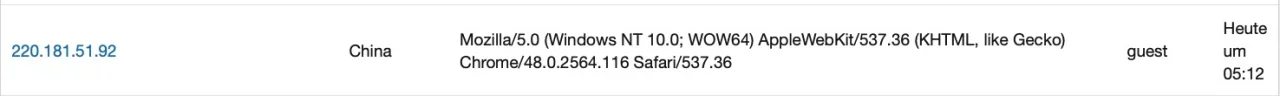
The IP is from China (which is country blocked in the settings of Thread Monitor) and belongs to an ASN that is blocked via ASN blocking. The whole ASN is well known for scraping and other malicious activities:
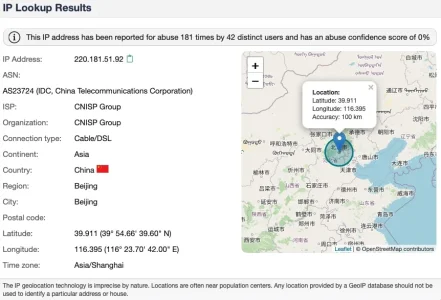
If one asks proxycheck.io they also state that this is malicious:
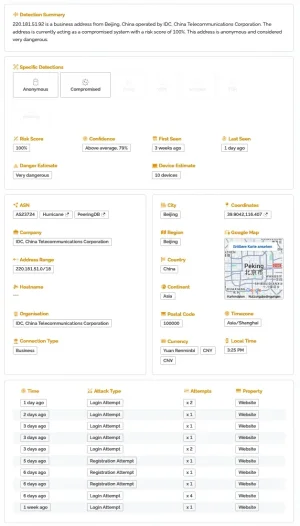
However: Not only is it not blocked by Threat Monitor, it even doesn't show up in the logs at all:
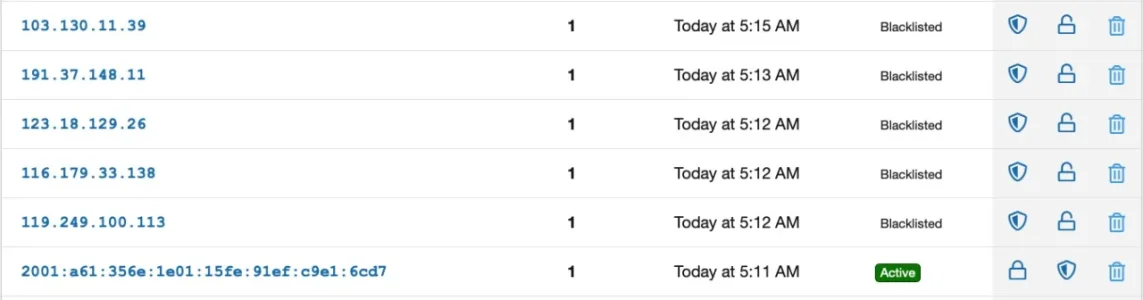
In opposite to that it shows up in my apache access logs quite frequently. This week alone:
grep 220.181.51.92 web.log | wc -l
68
grep 220.181.51.92 web.log | grep " 200" | wc -l
30
grep 220.181.51.92 web.log | grep " 301" | wc -l
31
grep 220.181.51.92 web.log | grep " 403" | wc -l
1
The request in question at 5:12 this morning went to scrape a thread and was followed by two others to other threads shortly after. All got a response "200" where they shout have got a "403":
220.181.51.92 - - [06/Feb/2026:05:12:05 +0100] "GET /threads/(...) HTTP/1.1" 200 20977 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/48.0.2564.116 Safari/537.36" 960 25337
220.181.51.92 - - [06/Feb/2026:05:26:11 +0100] "GET /threads/(...) HTTP/1.1" 200 16713 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/48.0.2564.116 Safari/537.36" 965 21072
220.181.51.92 - - [06/Feb/2026:06:44:12 +0100] "GET /threads/(...) HTTP/1.1" 200 16988 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/48.0.2564.116 Safari/537.36" 990 21347
So there would have been at least two if not three rules that should have stopped this IP accessing my forum - yet it came through and the logs show that it could grab content. Other well known nasty IPs from this block show the same pattern. Same goes for various IPs from other countries and other ASNs that have been blocked by either country or ASN or both but are not detected als malicious by proxycheck.io as they are resident proxies.
Any idea what the root cause my be? The only idea that came to my mnd is that my forum is reachable via both, IP v4 and IP v6 - but I've no idea if this has anything to do with it.
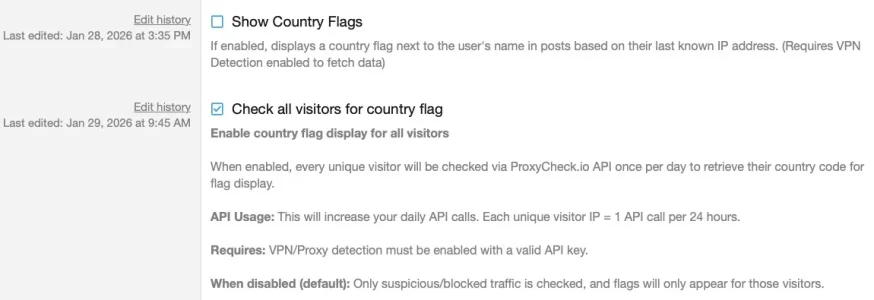
 2. Dealing with VPNs does not work as assumed
2. Dealing with VPNs does not work as assumed
While logged in users that come over an VPN stay unharmed guest visits via VPN don't behave like the settings say. These are the settings:
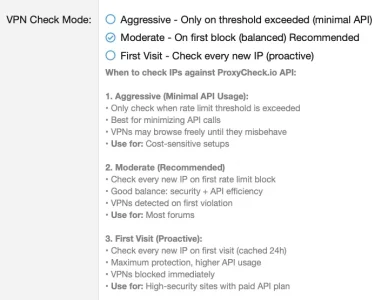
So, as I understand it, if no rate limits have been hit a visit via VPN should be possible. However: A check of guest access using Windscribe VPN resulted in an instant block:
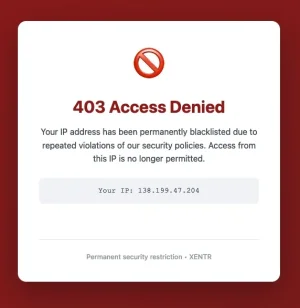
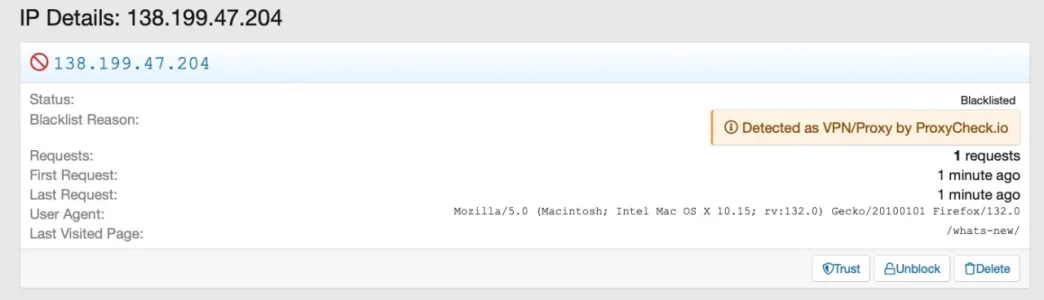
The same happened when testing via Opera Browser, using it's built in VPN-option from Opera themselves:
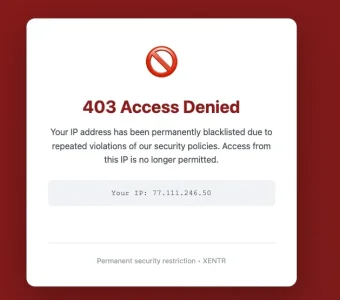
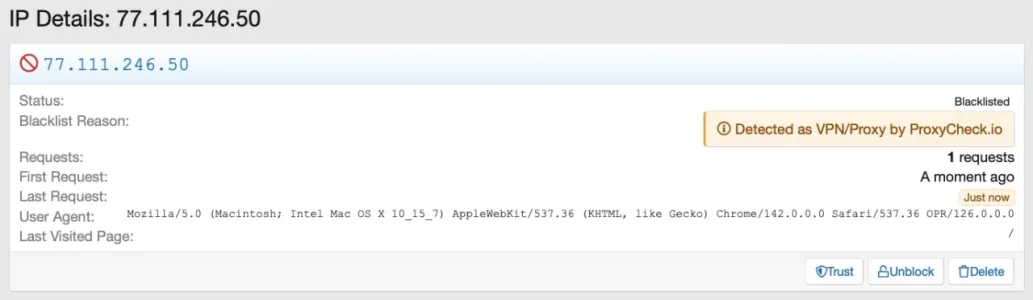
Regarding my understanding these requests should have com through.
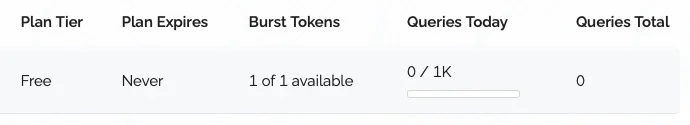
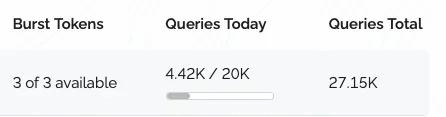
 3. Consumption of API calls seems quite excessive
3. Consumption of API calls seems quite excessive
As I am using the country flag and ASN detection one call per IP per 24h is to be expected. However: I consume typically 1,5 - 2,0 times the amount of API calls than IPs are listed on the dashboard. I.e. over the last 24h:
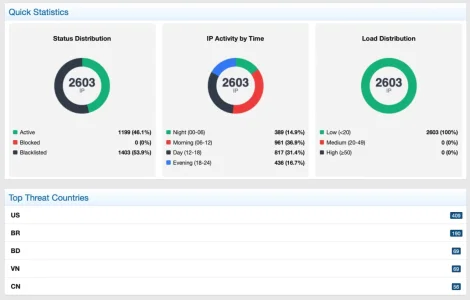
Those resulted in ~4.900 API calls consumed, according to the dashboard at proxycheck.io which seems a bit over the top. Is this normal or is something wrong here?
possible  4. Number of requests in the log is always 1
4. Number of requests in the log is always 1
After a week of use I've accumulated 256 pages of IP-Log and in total short of 13.000 IPS:

However: Not a single one does show more than one request which seems hard to believe. How are those counted
Questinons and suggestions will follow in the next post.