giorgino
Well-known member
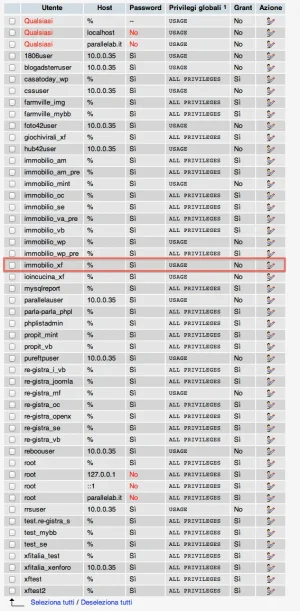
Hi all. I'm in trouble with one of my board.
The hacker modify my ad_header template with a malicious link
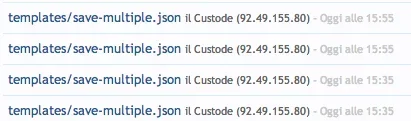
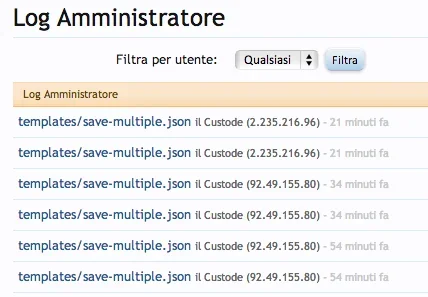
In my admin log:
What can I do?
The hacker modify my ad_header template with a malicious link
In my admin log:

Code:
array(12) {
["titleArray"] => array(1) {
[537] => string(9) "ad_header"
}
["styleidArray"] => array(1) {
[537] => string(1) "2"
}
["templateArray"] => array(1) {
[537] => string(356) "<!-- Inizio Banner Testata 728x90 -->
<div class="ad_header">
<!-- immobilio_728:90_header -->
<div id='div-gpt-ad-1338486582932-2' style='width:728px; height:90px;'>
<script type='text/javascript'>
googletag.cmd.push(function() { googletag.display('div-gpt-ad-1338486582932-2'); });
</script>
</div>
</div>
<!-- Fine Banner Testata 728x90 -->"
}
["addon_id"] => string(7) "XenForo"
["style_id"] => string(1) "2"
["template_id"] => string(3) "537"
["title_original"] => string(9) "ad_header"
["includeTitles"] => array(3) {
[1] => string(13) "ad_header.css"
[2] => string(9) "ad_header"
[3] => string(13) "ad_header.css"
}
["_TemplateEditorAjax"] => string(1) "1"
["_xfRequestUri"] => string(50) "/admin.php?templates/ad_header.537/edit&style_id=2"
["_xfNoRedirect"] => string(1) "1"
["_xfResponseType"] => string(4) "json"
}What can I do?