Mouth
Well-known member
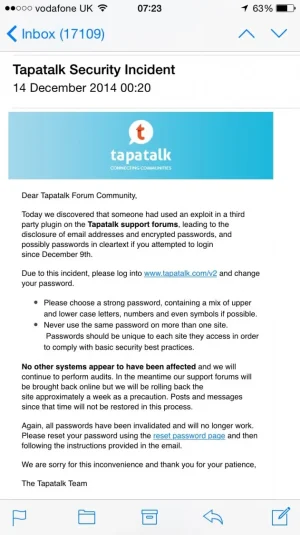
tapatalk said:Today we discovered that someone had used an exploit in a third party plugin on the Tapatalk support forums, leading to the disclosure of email addresses and encrypted passwords, and possibly passwords in cleartext if you attempted to login since December 9th.
Does anyone know which add-on? Has this been disclosed to XF?