For what I have learned reading you all, I understand this is not an XF issue, something which relieves me.
I have learned as well that there is a built-in spam filter which seems to work pretty well for what we are discussing about here.
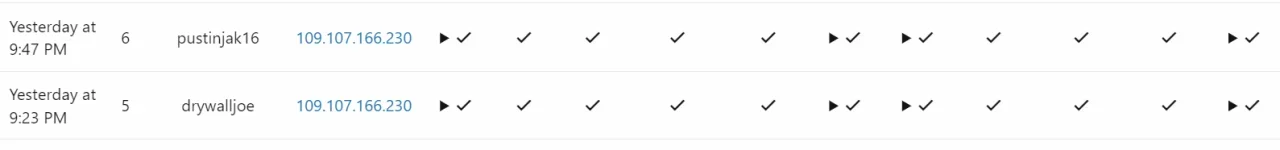
There are two IP addresses more that the Moldavian one, coming from the Netherlands but it seems they have stopped working in favour of the latter.
For what it's worth, this is what I have done:
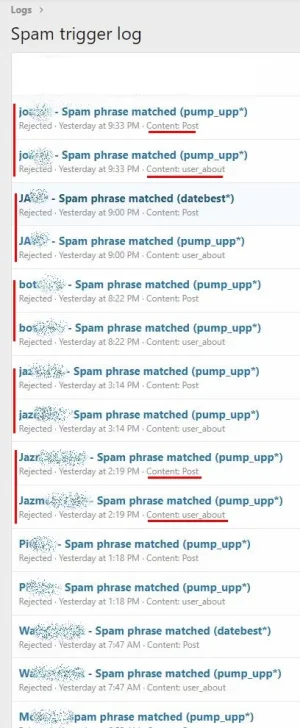
- added the key words to the SPAM management
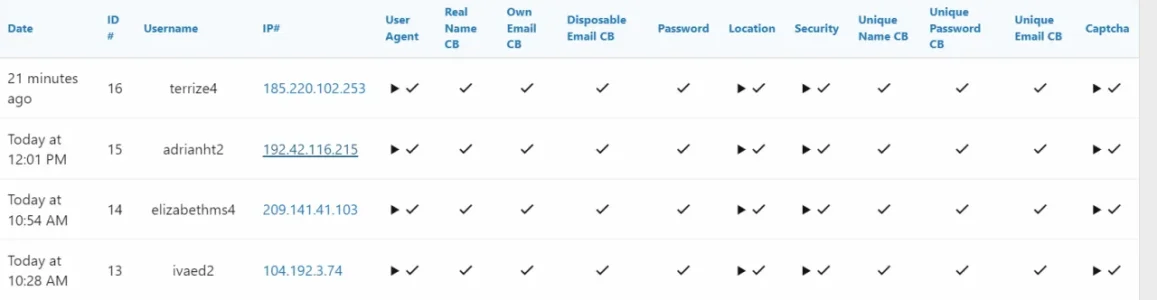
- looked at the spam log and changed the -few affected users to "must reset pwd"
- put that Moldavian IP in the "discouragement list"
This is the result of the first line (adding the keywords to the spam management):
View attachment 280424
By the way, it seems that the bot or whatever it is tries twice: first writing a reply in a random post, then to change the user's location. Both attemps were succesfully rejected.
And the best thing, these simple measures seem to have killed the problem, as we haven't been bothered since yesterday
Until they change the IP address or the "campaign" keywords. I know.