pattycake2
Active member
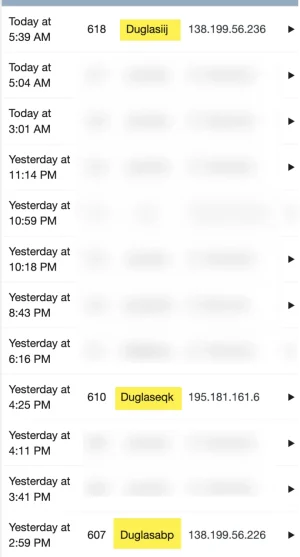
As we have noticed, these are dormant accts. I had another yesterday, again, dormant. Got to thinking... these dormant accts have never seen my xenforo site - they were imported from my vb conversion. That tells me me the breach is from a long time ago... well before I converted to XF. How many more of you converted to XF from vb, phpbb, or others?
btw: all of my incidents came from the same ip address. I originally banned the ip address, but have now un-banned it so I cam see if other usernames are exposed. On the ones that were hacked, all I did was manually change their password so I would see them in failed logins - did not change any levels
btw: all of my incidents came from the same ip address. I originally banned the ip address, but have now un-banned it so I cam see if other usernames are exposed. On the ones that were hacked, all I did was manually change their password so I would see them in failed logins - did not change any levels