oh wait... you have a library inside your library.. that's causing me confusion
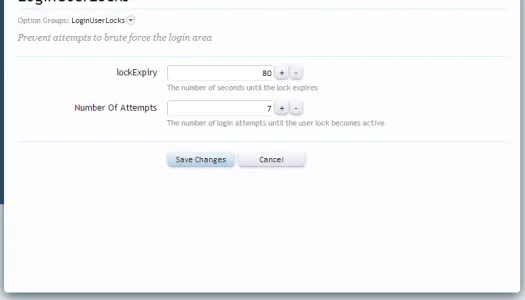
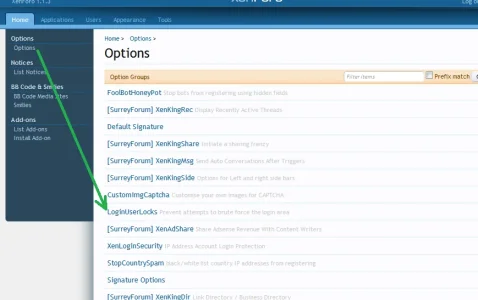
Delete LoginUserLocks_v1_0_1 from site folders and add the folder LoginUserLocks to your library
You possibly extracted the zip as "Extract to LoginUserLocks_v1_0_1", this means the LoginUserLocks is inside another folder named "LoginUserLocks_v1_0_1"
So, drag the folder named LoginUserLock into your library
Having that library folder inside a folder named library is going to confuse things
but your final file path should look like this:
yourforum/library/LoginUserLocks/
and inside that add the xml file, so that you have the path
library/LoginUserLocks/addon-LoginUserLocks.xml
Delete LoginUserLocks_v1_0_1 from site folders and add the folder LoginUserLocks to your library
You possibly extracted the zip as "Extract to LoginUserLocks_v1_0_1", this means the LoginUserLocks is inside another folder named "LoginUserLocks_v1_0_1"
So, drag the folder named LoginUserLock into your library
Having that library folder inside a folder named library is going to confuse things
but your final file path should look like this:
yourforum/library/LoginUserLocks/
and inside that add the xml file, so that you have the path
library/LoginUserLocks/addon-LoginUserLocks.xml