Interestingly, the Passkeys Google (and XenForo currently) creates on YubiKey IMHO somewhat contradict the definition used by FIDO alliance:This is what for example Google does - I can use a YubiKey 4 for 2FA but not for passwordless login

FIDO Passkeys: Passwordless Authentication | FIDO Alliance
Explore passkeys and how they provide phishing-resistant, passwordless login with faster sign-in and enhanced security. Start your passkey implementation.
 fidoalliance.org
fidoalliance.org
From a technical standpoint, passkeys are FIDO credentials that are discoverable by browsers
The Passkeys created by Google and XenForo on YubiKey are not resident/discoverable, eg. they can be used for passwordless login only if the credential is provided by the RP.
For XenForo this would require a change to the login flow, eg. even with such a Passkey the user would first have to enter the username/email so the credentials can be loaded from the server (just like it is done for 2FA).
Passkeys created via Android/Google Password Manager or iOS on the other hand are always discoverable and don't need the username first.
Passkey interoperability is really a mess with each option having advantages and disadvantages
With the current implementation of login flow:
userVerification discouraged, residentKey discouraged
userVerification discouraged, residentKey preferred
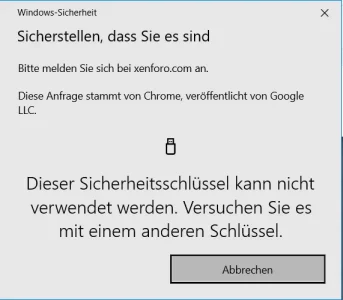
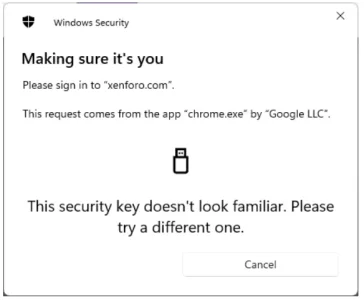
FIDO2 and U2F scecurity keys can be used for 2FA only.
userVerification preferred, residentKey discouraged
userVerification preferred, residentKey preferred
FIDO2 and U2F scecurity keys can be used for 2FA only; FIDO2 security keys will (most likely) setup/ask for PIN
userVerification required, residentKey discouraged
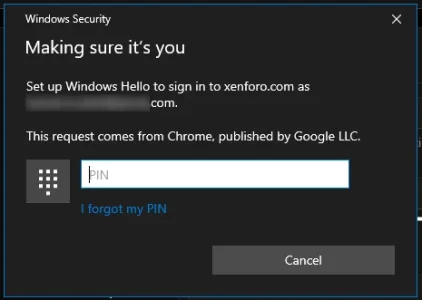
FIDO2 keys can be used for 2FA only and will setup/ask for PIN; U2F security keys can't be used.
userVerification required, residentKey required
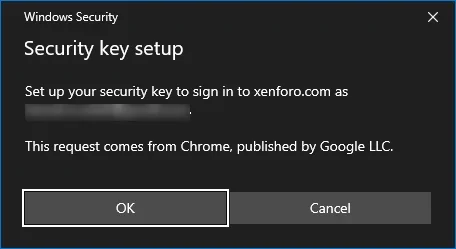
FIDO2 security keys can be used for login and 2FA, will setup/ask for PIN and store the credential.
Some users might want to have this behaviour, others may not as slots for resident keys are pretty limited (25 for YubiKey 5, 10 for NitroKey 3).
To cover most use cases XenForo would have to determine wether to use residentKey required or not before creating the credentiall:
- Use residentKey required if the user wishes to perform a login without entering username first using a FIDO2 security key
- Use residentKey preferred otherwise
Last edited: