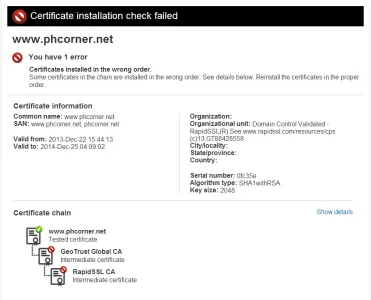
How can I fix this? 
Code:
nginx: [emerg] SSL_CTX_use_PrivateKey_file("/usr/local/nginx/conf/ssl/phcornernet/www_phcorner_net.key") fail ed (SSL: error:0B080074:x509 certificate routines:X509_check_private_key:key values mismatch)
nginx: configuration file /usr/local/nginx/conf/nginx.conf test failed