webbouk
Well-known member
Twice in the past week 287 js files within my forum and testforum (same server, different directories) have been reported as having 'Unexpected content', the latest event was today. Also the 'service_worker.js' and 'src/vendor/joypixels/emoji-toolkit/..'
I've restored them from a backup.
Is this something that is a result of a compromised server, or..... ?
CENTOS 7.9 [server] v94.0.8
As far as I'm aware the server is up to date and all security suggestions are implemented with the exception of JailApache
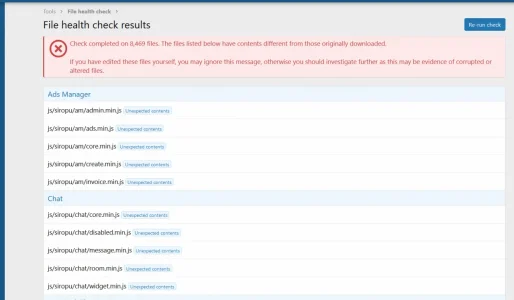
I've restored them from a backup.
Is this something that is a result of a compromised server, or..... ?
CENTOS 7.9 [server] v94.0.8
As far as I'm aware the server is up to date and all security suggestions are implemented with the exception of JailApache

Last edited:
