HammerDown submitted a new resource:
Cloudflare Firewall Rule: Ban Country Codes from Registration - Quickly add a Cloudflare Firewall Rule to block registration from specific countries.
Read more about this resource...
Cloudflare Firewall Rule: Ban Country Codes from Registration - Quickly add a Cloudflare Firewall Rule to block registration from specific countries.
Quickly add a Cloudflare Firewall Rule to block registration from specified countries.
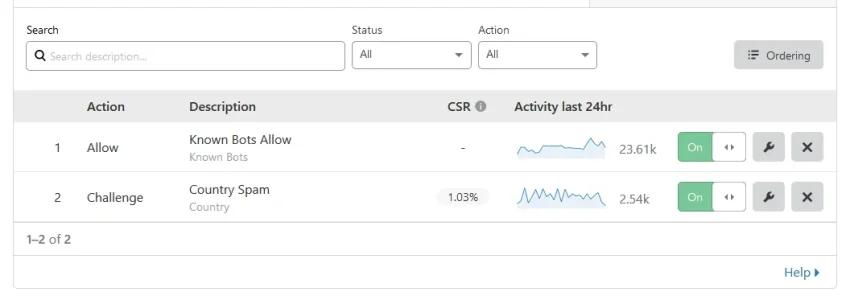
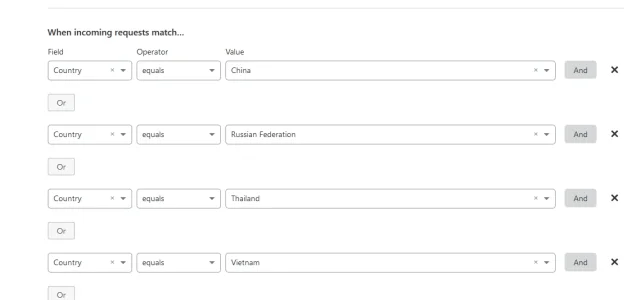
Go to Cloudflare > Firewall > Firewall Rules > Create a firewall rule
Look for small text link as you scroll down to Edit expression
Paste the following rule.
The action is Block.
Code:(ip.geoip.country in {"AF" "AL" "DZ" "AO" "AM" "AZ" "BD" "BJ" "BY" "BA" "BN" "KH" "CM" "BI" "CF" "TD" "CN" "CG" "CD" "DJ" "GQ" "ER" "ET" "GA" "GM" "GH" "HT" "IN" "IR" "IQ" "KZ" "KE" "KP" "KG" "KR" "XK"...
Read more about this resource...