V3NTUS
Well-known member
Hi,
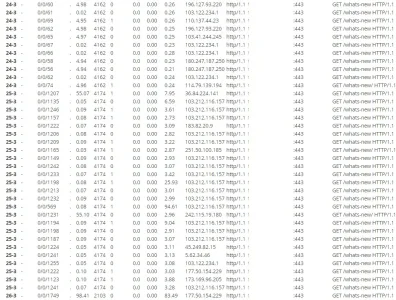
I'm having some issues as we're getting DDoS attacks and we noticed they're pointing a precise url: /whats-new/
Now, I know I can remove public access to the link by having the "What's New" menu vieweable only to registered users, but it doesn't solve the problem as it simply "hides" it (it can be still accessed via direct url), while I'm looking for a way to require users to be logged in to ACCESS this page.
For the moment, being still under attack and not finding any alternatives, I disabled the access to that page via .htaccess, but of course regular users can't access the page, too, this way, which isn't the ideal solution.
If there was a way to make the .htaccess recognize guests and/or registered members, it might work, but I think there must be a way to completely disable the /whats-new/ for guests via Xenforo Admin Panel.
Any ideas?
Thanks.
I'm having some issues as we're getting DDoS attacks and we noticed they're pointing a precise url: /whats-new/
Now, I know I can remove public access to the link by having the "What's New" menu vieweable only to registered users, but it doesn't solve the problem as it simply "hides" it (it can be still accessed via direct url), while I'm looking for a way to require users to be logged in to ACCESS this page.
For the moment, being still under attack and not finding any alternatives, I disabled the access to that page via .htaccess, but of course regular users can't access the page, too, this way, which isn't the ideal solution.
If there was a way to make the .htaccess recognize guests and/or registered members, it might work, but I think there must be a way to completely disable the /whats-new/ for guests via Xenforo Admin Panel.
Any ideas?
Thanks.