Floren
Well-known member
I was wondering if there are any users who have enabled SSL on their forums.
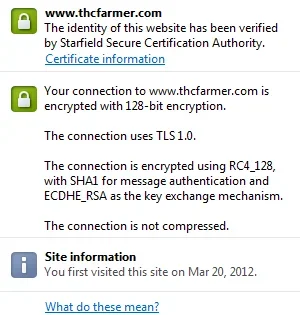
I recently switched one of my client's SSL to elliptic curves (EC) and the performance gains are simply stunning.
Pages load at least 50% faster, while the server load is reduced. Basically, is the same type of ciphers used on Google https sites.
Current setup uses OpenSSL 1.0.1c (EC enabled and combined with Google's 64-bit hacks/patches), Nginx 1.2.0, MariaDB 5.2.12 and PHP 5.3.13 running on CentOS 5.8. First thing I noticed was the improved First Byte time, under 2000ms for across the ocean requests.
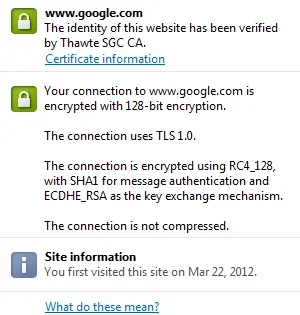
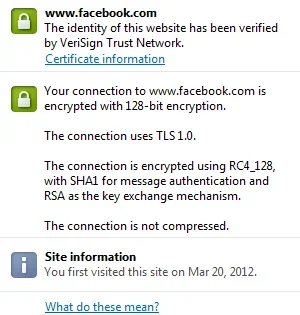
As far as I know, I did not see anywhere else the elliptic curve ciphers implemented beside Google.
Not even Facebook has it, which surprises me a lot:
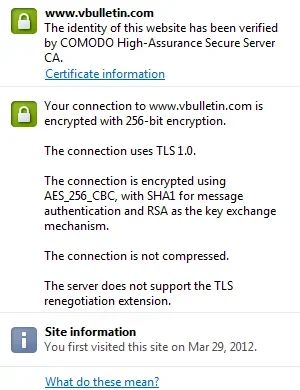
Please let me know what ciphers you use on your site and how do you find the overall performance with them.
If you could post some numbers, it will be great.
I recently switched one of my client's SSL to elliptic curves (EC) and the performance gains are simply stunning.
Pages load at least 50% faster, while the server load is reduced. Basically, is the same type of ciphers used on Google https sites.
Current setup uses OpenSSL 1.0.1c (EC enabled and combined with Google's 64-bit hacks/patches), Nginx 1.2.0, MariaDB 5.2.12 and PHP 5.3.13 running on CentOS 5.8. First thing I noticed was the improved First Byte time, under 2000ms for across the ocean requests.
As far as I know, I did not see anywhere else the elliptic curve ciphers implemented beside Google.
Not even Facebook has it, which surprises me a lot:




Please let me know what ciphers you use on your site and how do you find the overall performance with them.
If you could post some numbers, it will be great.