digitalpoint
Well-known member
It would be nice if XenForo has better handling of account security when something important on the account changes. For example, say an account was hijacked and the email address was changed.
First, it would just be nice is if the old email address was notified of the change. Even better would be if that email contained a link that allowed the recipient to undo the change (without authentication in case password was also changed). Link could be valid for a certain period of time (say 7 days).
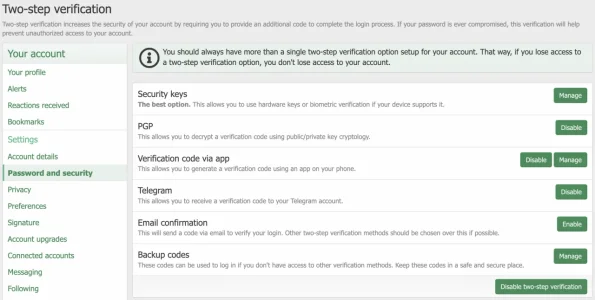
Notification of changes of any data that affects a user's ability to authenticate would be nice... email address change, password change, two-step auth changes, connected account addition/removal, etc.
First, it would just be nice is if the old email address was notified of the change. Even better would be if that email contained a link that allowed the recipient to undo the change (without authentication in case password was also changed). Link could be valid for a certain period of time (say 7 days).
Notification of changes of any data that affects a user's ability to authenticate would be nice... email address change, password change, two-step auth changes, connected account addition/removal, etc.
Upvote
30