MySiteGuy
Well-known member
Yes, I know this. Just missed it my overall reply.Hmm ... no.
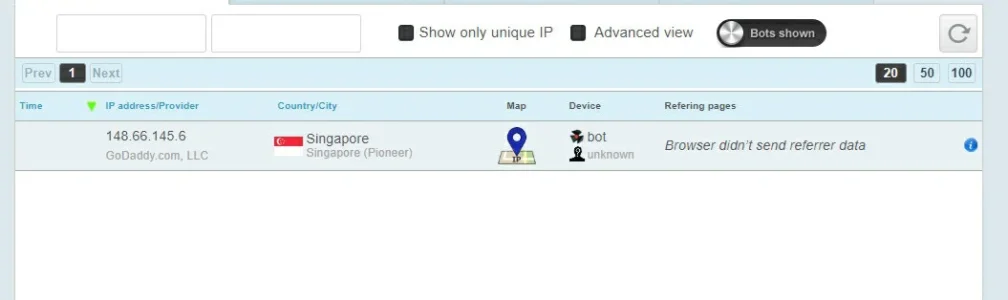
If a software just accepts user generated content containing external images but does not proxy them it would not leak the origin IP.
Yes, I know this, and the person who brought it up said it doesn't cover email.The Add-on does not cover all outgoing connections, just the two most common ones (image proxy and unfurl).
With enough effort an attacket probably could find other ways to trigger outgoing connections that would leak the origin IP (like RSS feed reader, push notifications, ...).
It seems you want to find fault in every answer, so my parting comment is: Good luck.