Ozzy47
Well-known member
I have not seen or used this yet, has anyone here used it?
Read more,
 thehackernews.com
thehackernews.com
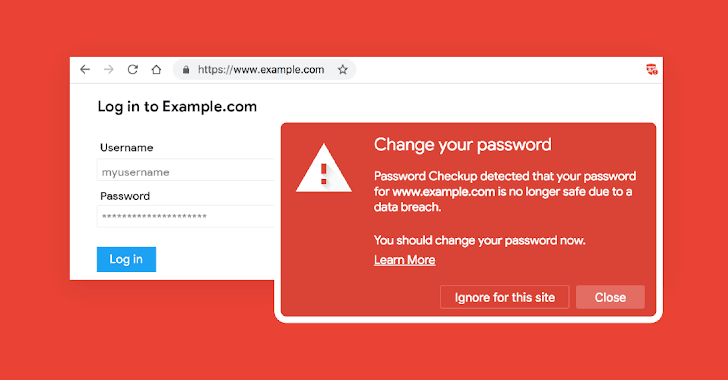
With so many data breaches happening almost every week, it has become difficult for users to know if their credentials are already in possession of hackers or being circulated freely across the Internet.
Thankfully, Google has a solution.
Today, February 5, on Safer Internet Day, Google launches a new service that has been designed to alert users when they use an exact combination of username and password for any website that has previously been exposed in any third-party data breach.
Read more,

Google's New Tool Alerts When You Use Compromised Credentials On Any Site
Google's New Password Checkup Chrome Extension Alerts When You Use Compromised Credentials On Any Site
 thehackernews.com
thehackernews.com
