Sheratan
Well-known member
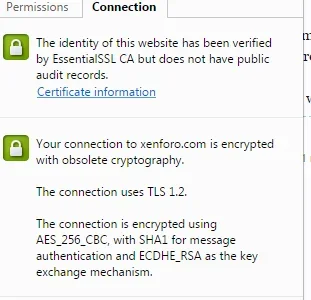
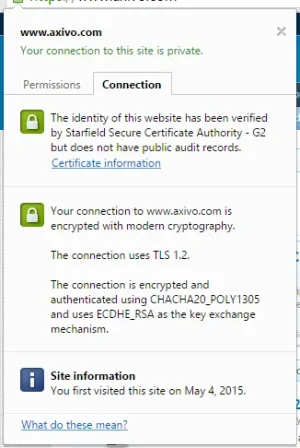
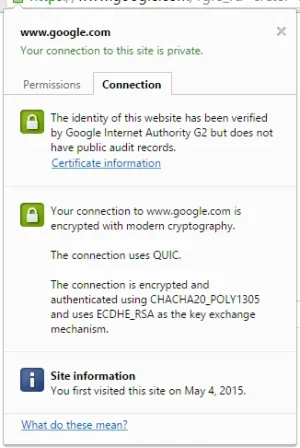
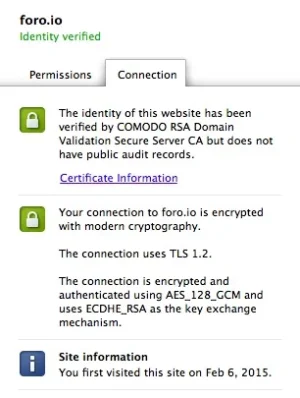
I just notice my site and xenforo in Chrome show this notification.
I read some article about that. It seems concerning about new encryption method, openssl version, and chiper suite. Too much to read for me
Anybody want to explain "what is that thing and how to fix that obsolete notification?"
I read some article about that. It seems concerning about new encryption method, openssl version, and chiper suite. Too much to read for me
Anybody want to explain "what is that thing and how to fix that obsolete notification?"