rosal
Active member
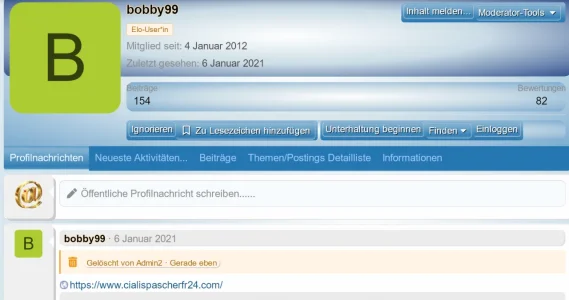
Since 3 January 2021 there is a bot targeting some platforms:
The bot enter in accounts and sometime change passwords.
IP- 178.137.16.56
Email - leonsio@gmail.com
Search for this IP in your forum to check if your forum has been targeted.
At this moment i dont know how the bot have the login data for the account users.
References over internet:
 www.abuseipdb.com
www.abuseipdb.com
 cleantalk.org
cleantalk.org
 cleantalk.org
cleantalk.org
- Xenforo 1.5x
- Xenforo 2.x
- Wordpress
- phpBB
- IPS Community Suite
The bot enter in accounts and sometime change passwords.
IP- 178.137.16.56
Email - leonsio@gmail.com
Search for this IP in your forum to check if your forum has been targeted.
At this moment i dont know how the bot have the login data for the account users.
References over internet:
178.137.16.56 | Kyivstar PJSC | AbuseIPDB
Email leonsio@gmail.com spam report
Email leonsio@gmail.com has no spam activity. IP Address spam activity, Whois Details, IP abuse report. Learn more.
IP 178.137.16.56 spam report. Blacklists & IP abuse DB
IP 178.137.16.56 has spam activity on 72 websites, history spam attacks. AS15895 spam rate 11.24%. IP Address spam activity, Whois Details, IP abuse report. Learn more.