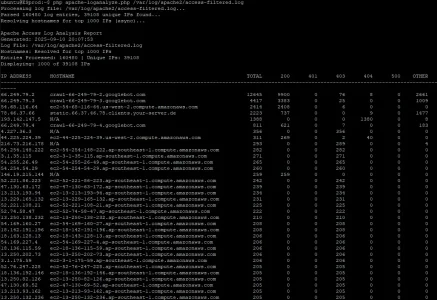
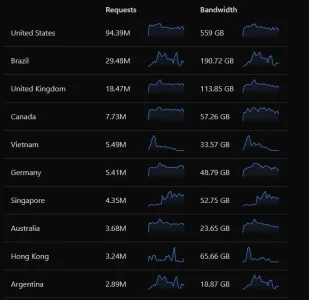
So my forum is now getting hammered by AI crawlers causing xf_session_activity to fill and stop the forum from loading. I've gotten over 10,000 unique ips.
Changing the table type to innodb is just a temporary bandaid.
I already have cloudflare blocking AI crawlers enabled but it doesn't work. The user-agents are all spoofing real browsers and the ips are all residential proxies.
The only thing that can stop them is to enable javascript verification for all users but this greatly annoys users.
Does anyone have a solution?
Changing the table type to innodb is just a temporary bandaid.
I already have cloudflare blocking AI crawlers enabled but it doesn't work. The user-agents are all spoofing real browsers and the ips are all residential proxies.
The only thing that can stop them is to enable javascript verification for all users but this greatly annoys users.
Does anyone have a solution?