alexD
Well-known member
No such thing as that would affect the SEO (the login form is normally present in all public facing pages - so that solution wouldn't help), please stand by.add no follow attribute to registration and log in via robot.txt?
No such thing as that would affect the SEO (the login form is normally present in all public facing pages - so that solution wouldn't help), please stand by.add no follow attribute to registration and log in via robot.txt?
i believe cloudflares free ssl suffices for this no?
Even that will still hide the issue instead of fix it, the traffic would be encrypted between the client and CloudFlare, but not CloudFlare and your server. They may have an option to use a self signed cert between CloudFlare and your server, not sure
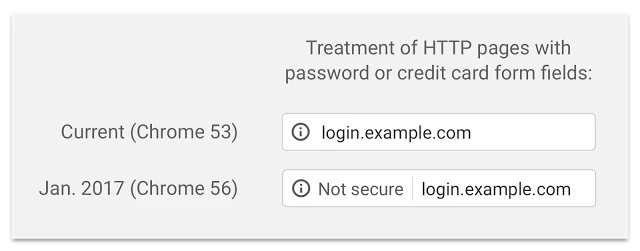
Firefox 51:Chrome is likely to catch things like opening the registration form in a modal
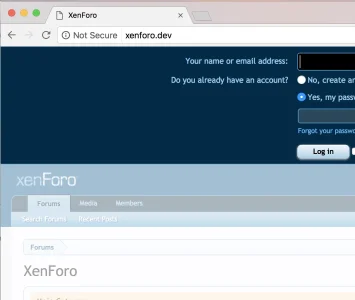
they released earlier today https://community.centminmod.com/posts/43732/January 31, 2017 will be when Chrome 56 is released. We plan to move to SSL the day before on our last site.
I'm not using Chrome 56, how does it show sites that are https but with mixed media content on login pages?
^^ This ^^The amount paid often reflects what kind of guarantee it comes with. Just getting TLS encryption at this point should be free or near free. If you are required to obtain a certificate that has verification then it will cost more. If you want liability insurance when you are breached then it's going to cost a fortune.
they dont support lets encrypt i asked

"Your notice of insecure password and/or log-in automatically appearing on the log-in for my website, Oil and Gas International, is not wanted and was put there without our permission," a person with the user name dgeorge wrote here. "Please remove it immediately. We have our own security system, and it has never been breached in more than 15 years. Your notice is causing concern by our subscribers and is detrimental to our business."
Some people are natural bozo's... and others are just pure natural ID10T's.https://arstechnica.com/security/20...for-labeling-unencrypted-login-page-insecure/
HAHAHAHA First off, NEVER assume you have never been breached. Second their 2001 web design hints to me they might not pay attention to web standard news, that they probably don't even have any real security team.
We use essential cookies to make this site work, and optional cookies to enhance your experience.