webbouk
Well-known member
Not my forum, this oneCheck the source of those guests
Not my forum, this oneCheck the source of those guests
I don't want to deviate from the main topic for which the thread was created, but I'll be honest: I don't know much about code, but I have a lot of experience in managing and maintaining websites. I tend to recommend products not based on the quality of the code (because I don't understand it very well) but on their effectiveness and efficiency, and in my humble opinion, @Ozzy47's addon does an excellent job. To be clear, I don't know and I don't know who @Ozzy47 is and I have no affiliation with him. But I believe his addon is an excellent solution for Xenforo spam. Xenforo itself already offers the best solutions to prevent spam and yet spammers still manage to bypass them. They do it on emails, on personal computers and on networks in general. So there will never be a 100% solution to prevent spam. Returning to your message; if they managed to bypass only two spammers, it is serious, but you should feel a bit more protected than those who don't have this addon installed.I've been running Ozzys addon for a whiile, but they still got through and logged into a dozen members. We are a subscription forum so most of the accounts they logged in with couldn't post. But they did generate spam for two subscribers.
I don't want to deviate from the main topic for which the thread was created, but I'll be honest: I don't know much about code, but I have a lot of experience in managing and maintaining websites. I tend to recommend products not based on the quality of the code (because I don't understand it very well) but on their effectiveness and efficiency, and in my humble opinion, @Ozzy47's addon does an excellent job. To be clear, I don't know and I don't know who @Ozzy47 is and I have no affiliation with him. But I believe his addon is an excellent solution for Xenforo spam. Xenforo itself already offers the best solutions to prevent spam and yet spammers still manage to bypass them. They do it on emails, on personal computers and on networks in general. So there will never be a 100% solution to prevent spam. Returning to your message; if they managed to bypass only two spammers, it is serious, but you should feel a bit more protected than those who don't have this addon installed.
I am saying that thes rogue logins have occurred while it was installed. If they have hacked emails and passwords of some members I wouldn't expect ozzys addon to stop them as they are not registering.
They are using my login Spaminator, th hat is stopping the bots from logging in.
Check the source of those guests.
My forum has been under unusually heavy traffic for several days, constantly having around 500-600 visitors from hundreds of IPs allocated to Microsoft in North America, and all with a Mac user agent, which is suspicious/unusual to the regular traffic (forum hosted in Germany targeting a cycling community in Romania). Ultimately I had to deny about 19 subnets in .htaccess. No idea what the purpose was; they were not trying to register or to post anything, maybe just scrape contents for an unknown reason, without identifying as a legitimate crawler.
Second traffic group is from bots attempting to register accounts (blocked by Cloudflare's new captcha) or to post as guests (did that successfully despite permissions set in Invision Power board prior to the migration to Xenforo). They are all coming from thousands of TOR exits/gateways, and I wish there was a nice way to identify them and block them automatically.
Neither of those seem related to the symptoms of the current issue of spam bots breaking into old forum accounts, though...
Perhaps these are the sessions checking old profiles for a name match, and the reasons I haven't had any successful logins is because I have that page locked down to unregistered group?
You made me curious, so I looked into the server's access log to see what URLs they were hitting. (Would be nice if Xenforo would give a hint to admins about the URL, not just that it's an error page.)I'm seeing the same thing from "Microsoft Des Moines", dozens per minute. This has been going on for a couple days.
Perhaps these are the sessions checking old profiles for a name match, and the reasons I haven't had any successful logins is because I have that page locked down to unregistered group?
Have you asked any of the users whose accounts have been compromised if they have used LastPass to store their passwords at any time in the past?Old users are being compromised (verified that was the case with the few of mine that got hit) and their profiles are being updated with the Telegram link in question.
I had been looking at getting at least one of the Spaminator addons, but couldn't figure out why I might need the Login Spaminator.Ahh the penny drops, I'm using the registration and was struggling to see how it would help
"Server log show some repetitive schema that spammers are using."Same thing here, mostly dormant but shared IP show also some moderators with 2FA enabled which is alarming !
Server log show some repetitive schema that spammers are using.
We anticipated dormant accounts becoming active spam, little time bombs just waiting to be armed and deployed... I'd seen it before back in the vB days...I had been looking at getting at least one of the Spaminator addons, but couldn't figure out why I might need the Login Spaminator.
Turns out, this week's activity is exactly why I need it
Any chance of next week's Lottery numbers
?
Coming from you, this sounds promising
I would rather leave it active so I can try and find out how this guy is getting in to these older dormant accts.
There is similar functionality in "DBTech Security" by @DragonByte Tech.is there an add-on that will send an alert or an email when an ip address is used to login to XF... like a way to monitor when this 109.107.166.230 logs in?
the problem is, he's not failing a login attempt... he somehow knows the password and logs right in. Thats why I need an alert whenever that ip address is used.There is similar functionality in "DBTech Security" by @DragonByte Tech.
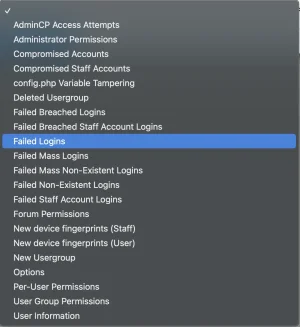
You can create "security watchers", e.g. for "Failed Logins":
View attachment 280200
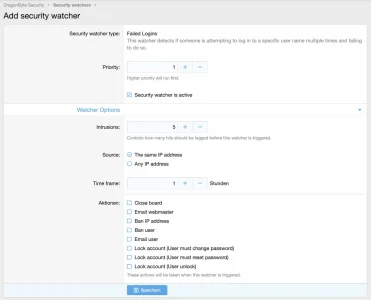
For failed logins, you can take several measures (also email webmaster):
View attachment 280201
Of course, this won't work, if the attacker uses a new ip address for every login.
sorry... not sure what this meansThey have the login information from data breaches.
We use essential cookies to make this site work, and optional cookies to enhance your experience.